Gene Expression Patterns ( IF 1.2 ) Pub Date : 2022-08-05 , DOI: 10.1016/j.gep.2022.119267 Yuyuan Sun , Chen-Ning Yang , Xuehu Yan , Yuliang Lu , Lei Sun
|
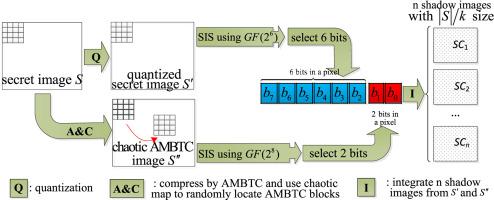
For (k, n)-threshold secret image sharing (SIS) scheme, only k or more than k complete parts can recover the secret information, and the correct image cannot be obtained if the count of shadow images is not enough or the shadow images are damaged. The existing schemes are weak in resisting large-area shadow image tampering. In this paper, we propose a robust secret image sharing scheme resisting to maliciously tampered shadow images by Absolute Moment Block Truncation Coding (AMBTC) and quantization (RSIS-AQ). The secret image is successively compressed in two ways: AMBTC and quantization. The sharing shadow images contain the sharing results of both compressed image from different parts, so that even the shadow images are faced with large-scale area of malicious tampering, the secret image can be recovered with acceptable visual quality. Compared with related works, our scheme can resist larger area of tampering and yield better recovered image visual quality. The experimental results prove the effectiveness of our scheme.
中文翻译:

强大的秘密图像共享方案抵抗 AMBTC 和量化的恶意篡改阴影
对于 ( k , n )-阈值秘密图像共享 (SIS) 方案,仅k或大于k完整的部分可以恢复秘密信息,如果阴影图像数量不足或阴影图像损坏,则无法获得正确的图像。现有方案对大面积阴影图像篡改的抵抗力较弱。在本文中,我们提出了一种强大的秘密图像共享方案,通过绝对矩块截断编码(AMBTC)和量化(RSIS-AQ)来抵抗恶意篡改的阴影图像。秘密图像通过两种方式依次压缩:AMBTC和量化。共享阴影图像包含来自不同部分的压缩图像的共享结果,因此即使阴影图像面临大范围的恶意篡改,也可以以可接受的视觉质量恢复秘密图像。与相关作品相比,我们的方案可以抵抗更大面积的篡改,并产生更好的恢复图像视觉质量。实验结果证明了我们方案的有效性。



























 京公网安备 11010802027423号
京公网安备 11010802027423号