Sādhanā ( IF 1.6 ) Pub Date : 2024-04-10 , DOI: 10.1007/s12046-024-02486-z V Nithya , S Senthilkumar , R Regan
|
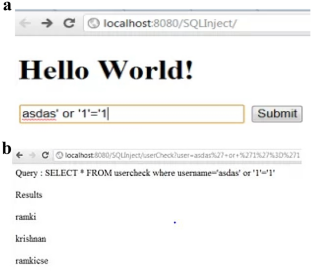
The landscape of application security presents an ongoing challenge due to the pervasive deployment of vulnerable web applications at a large scale. This perpetuates the susceptibility of compromising entire applications through easily exploitable entry points. Central to this issue is the prevalent absence of robust validation measures on both client and server side. Failure to adequately sanitize inputs leads to the emergence of Input Validation Attacks (IVA), encompassing threats like Structure Query Language Injection Attack (SQLIA), Cross Site Scripting (XSS), path traversal, and Command injection (CMDi). Security stands as a paramount concern within the application domain, especially considering that web application security constitutes a vital interface for interacting with computing systems and the expansive realm of the Internet. In light of these challenges, to enhance web application security through the implementation of hybrid analysis based static and dynamic deterministic pushdown automata, enriched by framework to proactively detect vulnerabilities and classify normal and abnormal request. While current solutions have proven effective in identifying web attacks, certain contexts necessitate a combined approach. Thus, the research work presents hybrid methodologies, further empowered by a machine learning paradigm. Then we evaluate feasibility of unsupervised approach for input validation attacks based rapid miner tool. The outcomes of our investigation exhibit notable advancement in accuracy and precision compared to established benchmarks. Our approach demonstrates a 2% enhancement over DEKANT, 5% over WAP, 10% over PhpMinerII, 53% over Pixy, and 20.2% over RIPS, over 0.4% than Ensemble learning model thereby underscoring its superior accuracy. Furthermore, it surpasses static taint analysis by of 21% in terms of precision.
中文翻译:

通过混合分析和机器学习简化输入验证攻击类型的检测
由于易受攻击的 Web 应用程序大规模普遍部署,应用程序安全形势提出了持续的挑战。这使得通过易于利用的入口点危害整个应用程序的可能性永久存在。这个问题的核心是客户端和服务器端普遍缺乏强大的验证措施。未能充分净化输入会导致输入验证攻击 (IVA) 的出现,包括结构查询语言注入攻击 (SQLIA)、跨站脚本 (XSS)、路径遍历和命令注入 (CMDi) 等威胁。安全性是应用程序领域中最重要的问题,特别是考虑到 Web 应用程序安全性构成了与计算系统和互联网广阔领域交互的重要接口。针对这些挑战,通过实施基于静态和动态确定性下推自动机的混合分析来增强 Web 应用程序安全性,并通过框架来主动检测漏洞并对正常和异常请求进行分类。虽然当前的解决方案已被证明可以有效识别网络攻击,但某些情况下需要采用组合方法。因此,这项研究工作提出了混合方法,并由机器学习范式进一步增强。然后我们评估基于快速挖掘工具的输入验证攻击的无监督方法的可行性。与既定基准相比,我们的调查结果显示准确性和精确度显着提高。我们的方法比 DEKANT 提高了 2%,比 WAP 提高了 5%,比 PhpMinerII 提高了 10%,比 Pixy 提高了 53%,比 RIPS 提高了 20.2%,比集成学习模型提高了 0.4% 以上,从而强调了其卓越的准确性。此外,它的精度比静态污点分析高出 21%。



























 京公网安备 11010802027423号
京公网安备 11010802027423号