Abstract
This paper investigates rumor transmission over online social networks, such as those via Facebook or Twitter, where users liberally generate visible content to their followers, and the attractiveness of rumors varies over time and gives rise to opposition such as counter-rumors. All users in social media platforms are modeled as nodes in one of five compartments of a directed random graph: susceptible, hesitating, infected, mitigated, and recovered (SHIMR). The system is expressed with edge-based formulation and the transition dynamics are derived as a system of ordinary differential equations. We further allow individuals to decide whether to share, or disregard, or debunk the rumor so as to balance the potential gain and loss. This decision process is formulated as a game, and the condition to achieve mixed Nash equilibrium is derived. The system dynamics under equilibrium are solved and verified based on simulation results. A series of parametric analyses are conducted to investigate the factors that affect the transmission process. Insights are drawn from these results to help social media platforms design proper control strategies that can enhance the robustness of the online community against rumors.
Similar content being viewed by others
1 Introduction
Over the past decade, rapid development of online social communities has made far and profound impacts on multiple aspects of the modern world. Unlike word-of-mouth communication networks or traditional news media (e.g., newspapers or television), online social networks (OSNs), such as those based on Facebook and Twitter, have changed the way how information is transmitted – users do not only behave as passive information receivers, but also have the liberty to generate or pass new content to others. Such an interactive mechanism makes information more accessible to all users, but at the same time also leads to difficulties in guaranteeing the reliability and truthfulness of transmitted contents. In certain cases, people with ignorance or foul intentions may even purposefully transmit rumors (i.e., unconfirmed elaboration or annotation of information that is of public interest (Wang et al. 2015)) to influence public opinions. For example, in January 2020, false information on possible ways to cure COVID-19, such as drinking detergent products, was widely transmitted in OSNs and resulted in hundreds of deaths (Islam et al. 2020). In recognition of the serious consequences that rumors may bring, the World Economic Forum listed “massive digital misinformation” as one of the top risks facing a modern society (Howell 2013).
Transmission of rumors and their negative social impacts can be largely attributed to the absence of administrative control over vicious and misleading information. Various methods that suggest optimal control exist in the literature. For example, a widely adopted control mechanism has been proposed for solving the Influence Maximization (IM) problem (Vega-Oliveros et al. 2020), where individuals that have a large impact on networks are identified. However, the effectiveness of these control methods crucially depends on the accuracy of the underlying mathematical model that describes the information diffusion process in OSNs. In fact, despite the abundance of data that most OSNs possess during their operation, there still lacks a method that generates accurate assessments of the status quo (especially for rumors that are still developing) that are necessary for efficient content screening strategies. In light of this need, quantitative models that describe rumor transmission mechanisms have become a popular interdisciplinary research topic, branching into studies of cloud-based multicasting mechanism (Wang et al. 2013), normative mechanism (Lee and Oh 2017), self-growth mechanism (Huo and Cheng 2019), etc. To the best of our knowledge, most of the previous efforts on this topic have not considered the decision-making processes of users with different psychological states and their influence on rumor transmission.
This paper aims to fill the above gaps by proposing a more comprehensive modeling framework for rumor transmission over OSNs.
-
1.
We introduce a directed graph to represent an OSN, which can not only effectively describe the directional transmission of rumors, but also accurately capture a user’s follower and followee numbers.
-
2.
We represent the mixed population with five compartmentsFootnote 1, namely the susceptible (S), the hesitating (H), the infected (I), the mitigated (M), and the recovered (R), and develop novel transmission rules to describe their transmission dynamics. Analytical formulas for the system dynamics equation, expressed in forms of a system of differential equations, as well as the effective reproduction number and the final compartment sizes, are derived.
-
3.
We further propose a heterogeneous transmission game to describe the decision-making process of a user on whether or not to react to a topic. Each user is assumed to be risk-averse while weighing a trade-off between expected popularity among followers and possible penalty from the social media platform for spreading false information.
-
4.
A series of numerical experiments, as well as parametric sensitivity analyses, are conducted to demonstrate the applicability of the proposed model, as well as to draw insights. Characteristics of the rumors and those of the users are examined to give a better understanding on their impacts on the rumor transmission process. Moreover, sensitivity analyses on various system parameters are also conducted; the findings can be used to design policies that can control rumor transmission toward certain objectives (e.g., containing the final influenced population, or limit the peak of transmission rate) under limited budget or resources.
The rest of this paper is organized as follows. s. Section 2 reviews the related work. Section 3 introduces the dynamics of an OSN system, with S, H, I, M, R compartments, and basic characteristics. Section 4 proposes a transmission game in which users interact with one another to reach an equilibrium condition. In Sect. 5, we verify the proposed model with simulations, and conduct a series of parametric sensitivity analyses. Lastly, we make final remarks in Sect. 6.
2 Related Work
In this section, we comment on the previous efforts that are related to the present article.
2.1 Rumor Transmission Model
Two widely adopted information diffusion models are the Linear Threshold Model (LTM)(Chen et al. 2010; Kempe et al. 2003) and the Independent Cascade Model (ICM)(Lu et al. 2017). The ICM is normally implemented in discrete time steps. Starting from an initial subset of nodes, the state of other nodes are changed by a cascade; i.e., an infected node will attempt to infect its susceptible neighbors and may succeed according to certain probability. Such a probability usually varies over edges to represent the relationship credulity. On the other hand, the LTM models this stochastic process in a slightly different manner. A node changes from susceptible state to infected state only when the frequency of receiving information from its neighbors is larger than a node-specific threshold(Zhu et al. 2014). Inspired by these basic models, while recognizing clear similarities between the transmission of rumors and infectious diseases (Gomez-Rodriguez et al. 2013), researches have been extensively exploring describing information diffusion via epidemiological models. In the 1920s, Kermack and McKendrick (1927) first modeled the infection dynamics of a disease, whereas the population is divided into three compartments: the susceptible, the infected and the recovered (SIR). The SIR model describes the state dynamics of nodes in a general system, and it sees adoption in a variety of application contexts, such as data transmissions in mobile Inter-vehicular communication networks (Mashwama et al. 2020), and dynamic emotion contagion in a crowd of evacuees (Xiang et al. 2018). After that, the development of various epidemiological models and mechanisms subsequently emerged, often assuming a well-mixed population that can be described by an SIR-type system dynamics (Daley and Kendall 1964; Maki and Thompson 1973; Sudbury 1985; Rey et al. 2016). Recently, Lu and Ouyang (2019) proposed a new epidemic dynamics model with a vaccination game to describe the influence of “vaccine-phobia” on the disease propagation process.
However, basic epidemiological models cannot fully represent the process of rumor transmission in OSNs due to different characteristics of the system (e.g., interaction mechanisms and graph structures) that drive more complex system dynamics. For example, information transmission in OSNs is typically directional, from leaders to followers, hence requiring descriptions based on directed graphs. In addition, rumor transmission depends on a much more subjective decision-making process that involves complex psychological factors of the participants; hence, the SIR-type dynamic system models need to be extended to capture the mental states (such as hesitation and reactions) of individuals.
These challenges were partially addressed in some of the studies on rumor transmission. On one hand, more complex population distributions, such as “scale-free networks” (Albert et al. 2000; Nekovee et al. 2007) and “small-world networks” (Zanette 2002; Lü et al. 2011), have been used to better describe the online community. These studies utilized the edge-based dynamics model proposed by Volz (2008) for random graphs (which was later simplified/extended by Miller (2011)). After that, many extended edge-based models were proposed to study the process of information transmission (Spencer and Srikant 2015; Xian et al. 2020), most of which nevertheless considered information transmission in undirected networks. On the other hand, dynamical systems with additional compartments (beyond S, I, and R), and those with multiple types of information, have also been developed to describe the diverse states and scenarios associated with participants in OSNs. Examples of the former include the Susceptible–Infected–Counterattack–Refractory model (SICR), which introduces the counter-rumor compartment and counterattack mechanism (Zan et al. 2014), and the Susceptible–Exposed–Infected–Recovered–Susceptible model (SEIRS-QV), with explicit consideration of vaccination and quarantine states (Hosseini and Azgomi 2018). Examples of the latter include the ignorant-spreader I-spreader II-stifler model (\(IS_1S_2R\)) model, with differentiation of information only in the propagation state (Zhuang et al. 2017), and the double SIR model (DSIR), where each type of information has its own complete dissemination process (Zan 2018). Muhlmeyer et al. (2020) summarized some previous dynamical systems and presented stochastic versions of these models.
2.2 Rumor Psychological Game
Efforts have also been made to address the psychological factors influencing rumor transmission in OSNs, mainly via the use of game theory that captures the decision-making process and interactions among different individuals. Zinoviev and Duong (2011) proposed a game-theoretic model for one-way information forwarding behavior in a star-shaped social network. Different participants, such as authorities (Zinoviev and Duong 2011) and rumor makers (Li and Liu 2016), were later added to the game to quantify their influence on rumor transmission. Etesami and Başar (2016) investigated a competitive transmission game for multi-information competition and communication over undirected networks. Recently, Huang et al. (2020) introduced a differential game-theoretic model by estimating the expected net utility of rumormongers and the expected loss of rumor victims. Moreover, it is typical to explicitly model people’s utility in order to understand the decision-making process under various human factors (such as cognitive behavior, psychology, neighbour influence) and popularity of information. These factors are further categorized as internal and external ones (Xiao et al. 2019). Internal factors include the number of followers (Wang et al. 2017), the emotional states (Li et al. 2020), the influence power of one individual (He et al. 2019) as well as the individual’s cognition, the self-interest in information and reputation (Qing and ZhengGong 2020). External factors often include herd psychology and herd pressure (Xiao et al. 2019; Yan and Jiang 2018).
Despite these efforts, two important aspects of the problem were missing in the literature. First, most of the proposed rumor transmission models are derived with undirected networks, implicitly assuming equal likelihood for either participant in a pair to influence each other. Such an assumption is not very realistic in modern OSNs; asymmetric information transmission in directed networks is much more realistic and generic, but has rarely been considered. Second, heterogeneous individuals’ rational decisions, and their collective potential to reach an equilibrium, have not yet been thoroughly considered. In particular, the number of followers is found to have a large impact on people’s transmission utilities, but to the best of the authors’ knowledge, such a mechanism has rarely been studied in the literature on rumor transmission.
3 SHIMR Model
This section introduces the proposed Susceptible-Hesitating-Infected-Mitigated-Recovered (SHIMR) model, a generalization of the classic SIR model (Kermack and McKendrick 1927) that explicitly considers human’s psychological behavior while facing rumors.
3.1 Model Formulation
In our model, we consider the joint transmission of a rumor and a counter rumor (i.e., opposite opinions or claims over an controversial topic), neither of which have evident support or authoritative endorsement. Online users are assumed ignorant (i.e., possessing no knowledge regarding the fact), have no inherent bias, and may possibly choose to believe and spread either opinion.
We consider a directed graph \(G(\mathcal {N},\mathcal {E})\) representing a social media network, where \(\mathcal {N}\) and \(\mathcal {E}\) stand for the sets of account nodes and communications arcs, respectively, and \(n = |\mathcal {N} |\). The network is simple (i.e., free of self-loops or multiple arcs between any pair of nodes, as explained in Newman et al. (2001)). The nodes in this graph are divided into five compartments:
-
1.
Susceptible nodes (S): those who are not yet exposed to the rumor or counter-rumor so far;
-
2.
Hesitating nodes (H): those who are aware of the controversial topic but have not decided whether to express an opinion;
-
3.
Infected nodes (I): those who have decided to spread the rumor;
-
4.
Mitigated nodes (M): those who have decided to spread the counter-rumor;
-
5.
Recovered nodes (R): those who are aware of, but have eventually lost interest in, the controversial topic.
For simplicity, we hereon denote the fractions of nodes in all five compartments over the entire population by S, H, I, M, R, respectively. Clearly,
Although a few spreaders must exist to initiate the discussion, the size of their population is assumed negligible at time \(t=0\), i.e., \(\frac{I(0)}{S(0)}\rightarrow 0\). Moreover, for any compartment \(A \in \{S, H, I, M, R\}\), we let \(A_{jk}(t)\) be the fraction of nodes in that compartment that have in-degree \(j\in \{1,...,J\}\) and out-degree \(k \in \{1,...,K\}\) at time t. We also let \(p_{jk}\) be the probability that an arbitrary node has degree-(j, k). Then, we have:
According to Newman et al. (2001), the distribution of degrees in a random network follows a power law (Fu et al. 2008), which can be expressed in the form of a probability generating function, as follows:
The average in-degree, \(\langle j \rangle\), and out-degree, \(\langle k\rangle\), are given as follows:
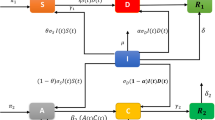
We assume that an \(S_{jk}\)-type node may receive the rumor (or counter-rumor) from one of its infected (or mitigated) neighbors according to a Poisson process with a constant rate \(r_I\) (or \(r_M\)). Upon being exposed to the topic, this node will transition into the H compartment immediately. The amount of time needed for an \(H_{jk}\)-type node to react follows a negative exponential distribution with parameter \(\beta\). This node decides to either transmit a pertinent opinion (rumor or counter-rumor), which occurs with probability \(\gamma _{jk}\), or stay silent and ignore the topic, which occurs with probability \((1-\gamma _{jk})\). This decision on whether to stay silent will be the result of a Nash equilibrium, which will be discussed in Sect. 3. If the node decides to transmit an opinion, it will spread the rumor with conditional probability q(t), or counter-rumor with probability \((1-q(t))\). These sequence of decisions will determine how this H node will transition into the corresponding compartment (i.e., I, M, or R). Finally, an \(I_{jk}\)-type (or \(M_{jk}\)-type) node may lose interest in the topic completely and transition into the R compartment with rate \(\mu _{I}\) (or \(\mu _{M}\)). All the abovementioned transition processes can be described as a decision tree, as illustrated in Fig. 1.
To simplify the analyses, we further assume that the network degree distribution remains approximately stable during the spread of the rumor (i.e., based on the Barabási–Albert model (Albert and Barabási 2002)). For convenience, we say that a node is in a certain compartment if it belongs to the corresponding compartment. Let \(\theta (t)\) be the probability that an arbitrary arc with an S-state successor has not transmitted an opinion by time t. Since transmissions on arcs occur independently according to a Poisson process, \(\theta (t)\) can be alternatively interpreted as the fraction of in-degree-one susceptible nodes at time t. We further differentiate the arcs by the state of its predecessor, using \(\theta _{S}\), \(\theta _{H}\), \(\theta _{I}\), \(\theta _{M}\), \(\theta _{R}\) to denote the corresponding probabilities. Obviously, we have
The transition process is illustrated in Fig. 2. An arc no longer satisfies the definition of \(\theta (t)\) as soon as the predecessor was in I- or M-compartment but has just transmitted an opinion to the corresponding S-state successor. Therefore, the change of \(\theta\) over time is captured as follows:
According to Volz (2008), the conditional probability for an arc to have an S-state successor and an I-state predecessor is \(\eta _I(t) = {\theta _{I}(t)}/{\theta (t)}\). Consider an S node with degree-(j, k), the expected number of arcs connected to I-state predecessors is then given by \(j \eta _I(t)\). We also define \(\eta _M(t)\) in a similar fashion for compartment M. As shown in Volz (2008), the fraction of degree-(j, k) nodes that still remain in S-state at time t (i.e., no transmission has ever occurred), denoted by \(u_{jk}(t)\), should satisfy the following differential equation:
which directly yields the explicit solution
With our assumed initial condition, i.e., \(u_{jk}(0)\rightarrow 1\), we can see that constant \(C_1 \rightarrow 1\).
Recall that \(\theta (t)\) is equal to \(u_{1k}(t) = \exp \{-\int _{\tau = 0}^{t} [r_I\eta _I(\tau ) + r_M\eta _M(\tau )] \ d\tau \}\). Therefore, the fraction of S-nodes with degree-(j, k) at time t is:
The dynamics of \(\theta _{I}(t)\) and \(\theta _{M}(t)\) are derived next. For an arbitrary target node, we use \(\xi _{jk}^{in}\) to denote the probability that any of its in-degree neighbors has degree-(j, k). This probability has an alternative interpretation – for an arbitrary directed arc with the target node as the successor, the probability that the predecessor of this arc has degree-(j, k). The total number of nodes with degree-(j, k) is \(p_{jk} \cdot n\), so the total number of out-going arcs from these nodes is \(p_{jk} \cdot n \cdot k\). Then, the probability that the predecessor of an arbitrary node has degree-(j, k) gives \(\xi _{jk}^{in}\), as follows:
Clearly, by definition, \(\theta _S(t)\) can be expressed as follows:
Note from Eq. (12) that \(\theta _S(t)\) = \([\sum _{j,\ k}kn{S}_{jk}(t)]\) \(/ [{\sum _{j,\ k}\langle k \rangle }n]\), i.e., the ratio of the total out-degrees from all \(S_{jk}\)-type nodes to the total out-degrees from all nodes in the network. We can derive \(\theta _{H}(t)\), \(\theta _{I}(t)\) and \(\theta _{M}(t)\) in a similar fashion as follows:
Using the aforementioned transmission rules, the dynamics of \(\theta _{I}\) consists of two parts: a positive term capturing a fraction of H-state nodes newly deciding to transmit the rumor, and a negative term indicating (a) a fraction of I-state nodes becoming stiflers and (b) successfully infecting an S-state node.
The dynamics of \(\theta _{M}\) can be derived similarly:
According to Knapp (1944), the probability of transmitting rumor is roughly in inverse proportion to the credibility of counter-rumor. Hence, we define the attractiveness difference between the rumor and the counter-rumor. To stay focused, we assume that the latter is closer to the fact, but the former is more appealing at its debut (especially when it is intentionally fabricated to be persuasive). As the public gradually reveals the truth, the rumor loses its attractiveness. Therefore, we assume the attractiveness difference of the rumor over counter-rumor, denoted \(\pi (t)\), gradually decreases over time from a large value of \(\pi _0\) until becoming completely stale with a small (or even negative) value of \(\pi _\infty\). We modify the functional form suggested in Zhang et al. (2018) and assume the following:
where v is the variation speed, and clearly \(\pi (0) =\pi _0\) and \(\pi (\infty ) = \pi _\infty\). We further assume the probability that node i chooses to spread the rumor, q(t), is related to \(\pi\) per the Fermi–Dirac statistics (McDougall and Stoner 1938) as follows:
Now, we are ready to summarize the dynamics of a degree-(j, k) node in all compartments, including Eqs. (7)-(10),(12)-(15) and the following:
3.2 Effective Reproduction Number
The effective reproduction number of an arbitrary test node at time t, denoted \(R_e(t)\), indicates the expected number of “infections” it can directly generate (Delamater et al. 2019). In our context, this quantity measures the transmission potential of a rumor topic and gives a necessary condition for a mass discussion “outbreak” to happen; i.e., if \(R_e(t) < 1\), the topic is expected to naturally die out without spreading to the entire population, and the opposite also holds. We follow the process proposed by Diekmann et al. (1990) to compute \(R_e(t)\). The detailed derivation in the appendix shows that an expression is given by
In particular, its value at \(t=0\), \(R_e(0)\), is also known as the basic reproduction number (Diekmann et al. 1990), which predicts the system’s vulnerability to a topic. Such vulnerability value serves as an effective check on the potential necessity for rumor control and intervention.
3.3 Final Compartment Sizes
At time \(t=\infty\), the value of \(A_{jk}(\infty )\) is the final fraction of degree-(j, k) nodes in compartment \(A \in \{S, H, I, M, R\}\). In particular, \(1 - S(\infty )\) measures the final size of the population influenced by the rumor or counter-rumor. Following Miller (2011), we show below how to derive formulas for these values when the probability of users receiving or discarding either opinion (rumor or counter-rumor) is equal, i.e. \(r_I = r_M = r\), and \(\mu _I = \mu _M = \mu\).Footnote 2
To this end, we define the “transmissibility” T as the probability that, conditional on the successor of an edge being in S-state and the predecessor in I or M-state, this edge successfully transmitted a pertinent opinion before its predecessor turns into state R. The transmissibility is given by \(T = \frac{r}{r + \mu }\). Further, we define \(\phi\) to be the probability that the predecessor of an arbitrary node has been in either I or M state. Recall from Eq. (11) that the probability for a predecessor of an arbitrary node to have degree-(j, k) is \(\frac{kp_{jk}}{\langle k \rangle }\), and the probabilities for this degree-(j, k) predecessor to ever be in the H state and to transmit an opinion, are \((1 - \theta (\infty ))^j\) and \(\gamma _{jk}\), respectively. Hence \(\phi\) is given by summing up the product of all these terms across for degree types; i.e.,
Clearly, the probability that an arbitrary edge with an S-predecessor has successfully transmitted opinion is given by \(T \cdot \phi\). Since every edge initially has an S-predecessor, this probability equivalently gives the fraction of the edges whose successors have been converted into the H state. By definition of \(\theta (\infty )\), we give the following expression
which is in the form of a fixed point if we define the right-hand-side as a function \(h(\theta (\infty ))\).
Hence, the fraction of nodes in different compartments at infinity time can be represented as follows:
4 Transmission Game in the H Compartment
In this section, we consider that a hesitating individual i in the H compartment with degree-(j, k) rationally makes decisions about whether to react to a topic. We assume all participants in the H compartment try to maximize their own utilities, and their willingness to transmit a rumor (or a counter-rumor) only depends on the benefits and penalties that result from the collective decisions of all OSN users. As we have many individuals of the same type, and they repeatedly deal with rumors, the decision-making strategy of each individual is specified by a Bernoulli probability distribution over the binary actions, with probability \(\gamma _{jk}^{i}\) for transmitting opinions.
Social media users mainly aim to gain popularity by increasing fan number, so that the users can enjoy public attention (Knapp 1944) or receive monetary reward through advertisement (Khamis et al. 2017). Generally, users realize this purpose by regularly making posts to appeal to their fans. Moreover, in order to quickly win fame or attention, some users decide to transmit controversial opinions. However, this risky action is a double-edged sword. Transmitting controversial opinions can also lead to the loss of fans. To reflect this phenomenon, we here define the utility as the public influence gained by posting controversial opinions. The utility consists of two parts:
In the first part, we define \(f_1(k, \gamma _{jk}^{i})\) as the expected popularity affected by fan numbers, which has a positive correlation with \(\gamma _{jk}^{i}\). Users with a small out-degree k are relatively more prone to transmitting controversial opinions in order to increase popularity. They are less risk averse. In contrast, those already popular (with a large out-degree k) are likely to be more conservative and risk averse. Hence, we assume that all users in the online social media follow risk averse behavior, which is represented by an increasing utility function with respect to \(\gamma _{jk}^{i}\). This function is also characterized by the coefficient \(\frac{k}{\alpha _1}\) to represent the degree of risk aversion, as follows (Guzavicius et al. 2014) :
Clearly when \(k\rightarrow \infty\) the utility function approaches zero.
Second, social media platforms may take the initiative to stop an opinion from transmitting in order to avoid offending certain user groups. This is commonly done by penalizing super-spreaders with account suspension or warning labels, often after the rumor propagation has ended. The severity of the expected penalty is assumed to be proportional to the impact of the topic, e.g., the final size of the influenced population \(R(\infty \mid \ \varvec{\gamma })\), where \(\varvec{\gamma } =\{\gamma _{jk}^{i}\}_{\forall i,j,k}\) denotes the decisions from the entire population. Moreover, the platform is assumed to be absolute risk-averse, and hence would naturally focus on penalizing popular accounts that spread the rumor. We assume that the coefficient of the penalty is monotonically increasing with the out-degree k as well as \(\gamma _{jk}^{i}\). When the platform is absolute risk-averse, the coefficient has a constant ratio of the second order derivative to the first-order derivative (with respect to \(\gamma _{jk}^{i}\) and k); a common choice would be taking an exponential form Pratt (1978). As such, we assume the coefficient satisfies the following \(e^{\ln \alpha _3 + \gamma _{jk}^{i}\frac{k}{\alpha _2}}\), where \(\alpha _2, \alpha _3\) capture the impacts of the platform’s penalty on the user’s utility. Further, in the derivation of Eq. (20) we see that the probability for a node to receive the penalty is \(\gamma _{jk}^{i}(1 - \theta (\infty \mid \ \varvec{\gamma })^j)\). Hence, the expected penalty of the \(i^{th}\) individual can be written as:
Putting Eqs. (23) and (24) together, the expected utility function for the \(i^{th}\) individual \(U_{jk}^i\) is as follows:
Note that \(U_{jk}^{i}(\gamma _{jk}^{i} \mid \ \varvec{\gamma })\) takes the same form and parameters for all the probabilistically identical users in a group with degree-(j, k). Intuitively, the strategy taken at equilibrium should thus be identical among each group, i.e., \(\gamma _{jk}^{i*} = \gamma _{jk}^{*}, \forall i\). Therefore, we can drop the superscript i in Eq. (25), and equivalently state the mixed Nash equilibrium conditions.
We are then ready to give the following statement on the existence and uniqueness of mixed Nash equilibrium.
Proposition 1
Consider the utility function given Eq. (25). A unique mixed Nash equilibrium is achieved when \(\{\gamma _{jk}^{*}\}_{\forall j,k}\) satisfies Eq. (26).
Proof
The existence of equilibrium is easy to see. Since \(\gamma _{jk}\) takes value from a closed domain [0, 1], and the objective function in Eq. (26) is continuous and bounded, there must exist a global maximum.
We then prove the uniqueness. For all \(k \ge 1\), it is easy to verify that the first order derivatives of Eq. (23) is positive and monotonically decreasing with respect to \(\gamma _{jk}\). Similarly, the first order derivative of Eq. (24) is also monotonically increasing with \(\gamma _{jk}\). Therefore, we see that the derivative of the utility function \(\frac{\partial }{\partial \gamma _{jk}} U_{jk}\) is monotonically decreasing with \(\gamma _{jk}\). It is also easy to verify that this derivative is positive at \(\gamma _{jk}=0\). Thus, there can be either one root \(\gamma _{jk}^{*} \in [0,1], \forall j,k\), where the utility function has a stationary point, or none, where \(\gamma ^{*}_{jk}=1, \forall j,k\) is the global maximizer. The latter case may happen if the topic is highly unlikely to spread out and have an impact (i.e., small \(R(\infty \mid \ \varvec{\gamma })\)), or if the platform lacks the credibility (i.e., small \(\alpha _3\)). In this case the transmitter bears little loss of its popularity from the penalty, thus would incline to transmit.\(\square\)
We are then ready to propose an algorithm to solve for this equilibrium, i.e., \(\varvec{\gamma }\) and \(\theta (\infty \mid \ \varvec{\gamma })\) (embedded in the computation of \(S_{jk}\)) satisfying Eqs. (26) and (21) simultaneously. Note that Eq. (21) defines \(\theta (\infty \mid \ \varvec{\gamma })\) in the form of a fixed-point \(\theta (\infty \mid \ \varvec{\gamma }) = h(\theta (\infty \mid \ \varvec{\gamma }))\), it is then natural to solve it through fixed-point iteration per Proposition 2 below.
Proposition 2
Eq. (21) is contract on \([0,\tilde{\theta }(\infty \mid \ \varvec{\gamma })]\). Further, the fixed-point \(\theta ^*(\infty \mid \ \varvec{\gamma })\) can be found by the fixed-point iteration with an initial guess \(\theta _0(\infty \mid \ \varvec{\gamma }) \in [0,\tilde{\theta }(\infty \mid \ \varvec{\gamma })]\).
Proof
According to Hale et al. (2008), evaluating Eq. (21) at \(\theta (\infty \mid \ \varvec{\gamma }) = 0\) and 1 gives \(h(1)=1\) and \(h(0)\in (0,1]\). In addition, \(h(\theta (\infty \mid \ \varvec{\gamma }))\) is monotonically increasing and convex. There thus exists two fixed points \(\theta ^*(\infty \mid \ \varvec{\gamma })\) and 1, with \(0< \theta ^*(\infty \mid \ \varvec{\gamma }) < 1\). Using the mean value theorem, there must exist a point \(\tilde{\theta }(\infty \mid \ \varvec{\gamma }) \in [\theta ^*(\infty \mid \ \varvec{\gamma }),1]\) such that
It then directly follows that \(h'(\theta (\infty \mid \ \varvec{\gamma })) < h'(\tilde{\theta }(\infty \mid \ \varvec{\gamma }))=1 , \forall \ \theta (\infty \mid \ \varvec{\gamma }) \in [0,\tilde{\theta }(\infty \mid \ \varvec{\gamma }))\). According to the Banach fixed-point theorem, starting from an initial guess \(\theta _0(\infty \mid \ \varvec{\gamma }) \in [0,\tilde{\theta }(\infty \mid \ \varvec{\gamma })]\), fixed point \(\theta ^*(\infty \mid \ \varvec{\gamma })\) can be found through iterations. The proof is complete.\(\square\)
Given an initial solution \(\varvec{\gamma }\), the algorithm proceeds by iteratively solving for \(\theta (\infty \mid \ \varvec{\gamma })\) using a fixed-point method, and \(\varvec{\gamma }\) using a bi-section method. Each element of the initial \(\varvec{\gamma }\) can be arbitrarily selected in [0, 1]. The integrated algorithm proceeds by solving for \(\gamma\) and \(\theta _\infty\) iteratively. The algorithm is described as follows:

5 Numerical Simulation and Discussions
5.1 Validation of Analytical Model
We consider a social network with heterogeneous users in an instance of wide-spreading topic (e.g., COVID-19). We conduct a series of simulations and use the results to verify the SHIMR model by predicting the evolution of the system during the transmission. The simulation assumes a power-law degree distribution for the number of fans of each individual (Huang and Su 2013). The maximum value of in- and out-degrees is set to \(J = K = 1000\).
The following parameters are used for the system: \(r = 0.03\), \(\mu = 0.01\), \(\beta = 0.01\), \(\alpha _1 = 12\), \(\alpha _2 = 8\), \(\alpha _3 = 0.01\), \(v=2, \pi _0= 61, \pi _\infty = -39\). Moreover, the initial condition at time \(t = 0\) is set as \(S(0) = 0.999\) and \(I(0) = 0.001\). We then conduct Monte Carlo simulations over random instances of a network with 10000 total nodes, which are generated using the Molloy–Reed algorithm (Molloy and Reed 1995). A total of 100 simulations are conducted, with 20 random runs over each of 5 generated networks. We randomly assign 10 rumor-spreaders at time \(t = 0\) to activate the transmission, and null initialization for other states, i.e., \(I(0) = 10\), \(S (0) = 9990\), \(H(0) = 0\), \(M(0) = 0\), \(R(0) = 0\).
The comparison of the model prediction the simulated benchmark is shown in Fig. 3. The solid lines show the predicted evolution of the compartments in the SHIMR model. The dashed lines and the shadow areas describe the corresponding means and \(95\%\) confidence intervals from 100 simulations. As shown, the model prediction of each compartment is in good accordance with the simulation result. The final epidemic size \(R_\infty\) computed from system dynamic model is 0.9903 and that from simulation is 0.9804, yielding a 1.01% relative difference. The peak values of predicted I and M compartments are 0.1977 and 0.1540 while the simulated peaks are 0.2023 and 0.1492, and the relative differences are 2.27% and 3.22%, respectively. These results demonstrate the fidelity of the formulas from the SHIMR model.
5.2 Sensitivity Analyses on Decision Game
To further observe the equilibrium of the decision game, we examine the stationary solution for each user group. While \(\{\gamma _{jk}^{*}\}_{\forall j,k}\) is numerically solved, we note from Eq. (26) that the individual decision at equilibrium should depend on the connectivity of this node. We plot the distribution of probability \(\gamma _{jk}\) in Fig. 4(a) over the in- and out-degrees. The value clearly decreases rapidly with respect to the out-degrees because popular users put more values on their popularity. Particularly, there is an abrupt change of \(\gamma _{jk}\) value between \(10-100\) out-degrees. The marginal impacts of additional out-degrees diminishes beyond that change.
In contrast, the trend over in-degrees is not so obvious, partially due to the setup of our utility functions. This is also due to the small value of \(\alpha _3\), which corresponds to the case that social media platform has little influence on suppress rumor spreading. Now, we select a larger \(\alpha _3\) and plot the zoomed-in view in Fig. 4(b). In this figure, \(\gamma _{jk}\) decreases with the in-degree slowly. Users that tend to transmit opinions are clustered, all with small out-degrees (which also consist of the majority of the population according to the power-law distribution). Therefore, if the social media platform wish to discourage users from participating in the mass discussion, it shall pay attention to those users with small out-degrees.
It is necessary to understand how the system will behave from a macroscopic perspective. We observe how the effective production number \(R_e(0)\) changes with respect to parameters \(\alpha _1,\alpha _2,\alpha _3\), as shown in Fig. 5. With larger \(\alpha _3\), the initial momentum of transmitting the topic in this social media platform is reduced. In both figures, \(\alpha _2\) has more influence than \(\alpha _1\). The results suggest that it is better to strengthen the influence of the platforms than to rely on the rationality of individuals on popularity. Additionally, the gradient is steeper at small \(\alpha _2\). Since \(\alpha _2\) indicates the inclusiveness of an enforcement (e.g., the minimum threshold of followers to be inspected for foul posts), we see that penalty-based controls are more effective when imposed on small and scattered accounts.
5.3 Sensitivity Analyses on Human Factors
To have a more in-depth understanding of the overall transmission process, we further investigate some hyper-parameters. We are interested in characteristics of human behavior (r, \(\mu\), \(\beta\)) and the credibility of the social media platform (\(\alpha _3\)). Figure 6 shows the peak magnitude of I compartment (\(I_{max}\)) and the time reaching the peak (\(t_{I_{max}}\)) when r, \(\beta\), \(\mu\) and \(\alpha _3\) range from 0.01 to 0.3. For simplicity, we only show simulation results here.
Higher values of r and \(\beta\) both foster wide transmitting of a rumor in a similar fashion, as the corresponding peaks of “infected” population increase and are reached earlier. Therefore, to alleviate the surges of the infection, it is beneficial to consider (1) reducing \(\beta\) by enhancing general education on internet moral and safety (which reduces emotional and blind decision-making), and (2) reducing r through browser censoring or lowering recommendation rate of disputable posts. However, note that the curves for these parameters are steeper at small values, indicating a large marginal gain only when these measures are taken to an extreme extent or the population is already very well educated.
On the other hand, the peak size of I compartment diminishes rapidly with \(\mu\) due to its significant role in removing I-state nodes. Thus it is effective to timely broadcast authorized alarm or clarification so that the public tends to be vigilant and willing to avoid discussing the topic. The curve is most steep when \(\mu\) takes value between 0.01 and 0.05, suggesting significant effectiveness in that range. The impact of \(\alpha _3\) is almost linear. This can be considered by the social media platform to achieve penalty effectiveness by strengthening its impact.
Similarly, the final influenced compartment size \(R(\infty )\), as well as those who have believed in the rumor and transmitted it (denoted \(R_I(\infty )\)) are shown in Fig. 7.
If containing the size of \(R_I(\infty )\) is the objective, the policymaker can reduce r and \(\beta\). This may be an effective option when the system currently falls in the steep region, although the overall difference is not significant. Alternatively, the policymaker can consider increasing \(\mu\) or \(\alpha _3\) which yields a linear marginal gain. It is noteworthy that \(\mu\) is the only parameter that has a significant impact, while other parameters have relatively negligible impacts. Recall the discussion over Fig. 6. It appears that prospectively educating the online community (i.e., reducing r and \(\beta\)) is less effective than post-reaction (e.g., by debunking rumor and punishing spreaders).
6 Conclusion
In this paper, we propose an SHIMR model to predict rumor transmission in a modern social network. The social network is represented by a random directed graph where each node indicates a user, and the in- and out-degrees follow a power-law distribution. The population is categorized, according to the stage of experiencing a rumor, into five compartments (i.e., S, H, I, M, R). The system dynamics is expressed, based on an edge-based formulation, as a set of ordinary differential equations. Furthermore, the effective reproduction number and the final compartment size are derived in closed form to capture the rumor’s tendency to propagate and its ultimate influence. A decision game is designed to describe how users rationally decide either to react to or disregard the ongoing rumor, whereas potential benefits and risks in transmitting an opinion are considered in the utility function. Then, the paper discusses conditions under which a Nash equilibrium can be reached among the OSN users, its uniqueness, and how to efficiently solve it via a fixed-point iteration and bisection search. The derived formulas and equilibrium solutions are validated with simulations. It is shown that the proposed SHIMR transmission model successfully predicts the rumor and counter-rumor transmission process. A series of experiments are conducted to illustrate the effects of various system parameters on the overall rumor transmission process. The result provides insights that could aid the design of policies and control strategies to achieve certain objectives, such as confining peak “infection” rate or final influenced population.
This paper paves the way for many future research directions. First, this study uses Monte Carlo simulations (as the ground truth) to verify the system dynamics predicted by our model. In future research, real-world data from social networks (e.g., traces of an opinion in Twitter or Weibo) should be used for model calibration and validation. Second, the model provides predictive power on rumor propagation, which can serve as a building block to design optimal control strategies that can resist turmoils. Dynamic and adaptive control laws may be established for timely interventions, especially in early stages of rumor development. Third, findings from this research could also be combined with efforts on improving compartment observability in real time, such as classifying the content of user posts through machine learning for statistical inference. Fourth, in this work, only one type of rumor is considered. Another direction of research, therefore, could look into extending the model towards more complex and realistic instances, where multiple interrelated rumors may emerge and transmit simultaneously, through one or multiple OSN platforms. The proposed modeling framework (and conclusions) may even be applied to systems in other application contexts, as long as they involve interdependent decision makers with dynamically changing states, such as those related to traffic congestion and equilibrium in a transportation network.
Data Availability
All data generated or analysed during this study are included in this published article.
Notes
In this paper, we follow the epidemiology and disease literature (e.g., see Angstmann et al. (2016) and Liu et al. (2019)) and use the word “compartment” to represent the subset of network nodes that are in one of the states. We could have instead used other terminologies (such as “subset”) throughout the paper.
Such a condition may be reasonable if the title of a post in social media does not provides sufficient information on the credibility of its content, or if most accounts have a regular schedule of deleting (or forgetting) dated posts.
References
Albert R, Barabási AL (2002) Statistical mechanics of complex networks. Rev Mod Phys 74(1):47. https://doi.org/10.1103/RevModPhys.74.47
Albert R, Jeong H, Barabási AL (2000) Error and attack tolerance of complex networks. Nature 406(6794):378–382. https://doi.org/10.1038/35019019
Angstmann CN, Henry BI, McGann AV (2016) A fractional-order infectivity SIR model. Phys A 452:86–93. https://doi.org/10.1016/j.physa.2016.02.029
Chen W, Yuan Y, Zhang L (2010) Scalable influence maximization in social networks under the linear threshold model. In: 2010 IEEE International Conference on Data Mining, IEEE, pp 88–97, https://doi.org/10.1109/ICDM.2010.118
Daley DJ, Kendall DG (1964) Epidemics and rumours. Nature 204(4963):1118. https://doi.org/10.1038/2041118a0
Delamater PL, Street EJ, Leslie TF, Yang YT, Jacobsen KH (2019) Complexity of the basic reproduction number (R0). Emerg Infect Dis 25(1):1. https://doi.org/10.3201/eid2501.171901
Diekmann O, Heesterbeek JAP, Metz JA (1990) On the definition and the computation of the basic reproduction ratio (R0) in models for infectious diseases in heterogeneous populations. J Math Biol 28(4):365–382. https://doi.org/10.1007/BF00178324
Etesami SR, Başar T (2016) Complexity of equilibrium in competitive diffusion games on social networks. Automatica 68:100–110. https://doi.org/10.1016/j.automatica.2016.01.063
Fu F, Liu L, Wang L (2008) Empirical analysis of online social networks in the age of web 2.0. Physica A 387(2-3):675–684, https://doi.org/10.1016/j.physa.2007.10.006
Gomez-Rodriguez M, Leskovec J, Schölkopf B (2013) Modeling information propagation with survival theory. International Conference on Machine Learning, PMLR 28:666–674
Guzavicius A, Vilkė R, Barkauskas V (2014) Behavioural finance: Corporate social responsibility approach. Procedia Soc Behav Sci 156:518–523. https://doi.org/10.1016/j.sbspro.2014.11.232
Hale ET, Yin W, Zhang Y (2008) Fixed-point continuation for l1-minimization: Methodology and convergence. SIAM J Optim 19(3):1107–1130. https://doi.org/10.1137/070698920
He Q, Wang X, Yi B, Mao F, Cai Y, Huang M (2019) Opinion maximization through unknown influence power in social networks under weighted voter model. IEEE Syst J 14(2):1874–1885. https://doi.org/10.1109/JSYST.2019.2922373
Hosseini S, Azgomi MA (2018) The dynamics of an SEIRS-QV malware propagation model in heterogeneous networks. Phys A 512:803–817. https://doi.org/10.1016/j.physa.2018.08.081
Howell L (2013) Digital wildfires in a hyperconnected world. WEF report 3(2013):15–94
Huang DW, Yang LX, Li P, Yang X, Tang YY (2020) Developing cost-effective rumor-refuting strategy through game-theoretic approach. IEEE Syst J 15(4):5034–5045. https://doi.org/10.1109/JSYST.2020.3020078
Huang J, Su Q (2013) A rumor spreading model based on user browsing behavior analysis in microblog. In: 2013 10th International Conference on Service Systems and Service Management, IEEE, pp 170–173, https://doi.org/10.1109/ICSSSM.2013.6602630
Huo L, Cheng Y (2019) Dynamical analysis of a IWSR rumor spreading model with considering the self-growth mechanism and indiscernible degree. Phys A 536:120940. https://doi.org/10.1016/j.physa.2019.04.176
Islam MS, Sarkar T, Khan SH, Kamal AHM, Hasan SM, Kabir A, Yeasmin D, Islam MA, Chowdhury KIA, Anwar KS et al (2020) Covid-19-related infodemic and its impact on public health: A global social media analysis. Am J Trop Med Hyg 103(4):1621. https://doi.org/10.4269/ajtmh.20-0812
Kempe D, Kleinberg J, Tardos É (2003) Maximizing the spread of influence through a social network. In: Proceedings of the ninth ACM SIGKDD international conference on Knowledge discovery and data mining, pp 137–146, https://doi.org/10.1145/956750.956769
Kermack WO, McKendrick AG (1927) A contribution to the mathematical theory of epidemics. Proc R Soc Lond A 115(772):700–721. https://doi.org/10.1098/rspa.1927.0118
Khamis S, Ang L, Welling R (2017) Self-branding, ‘micro-celebrity’ and the rise of social media influencers. Celebr Stud 8(2):191–208. https://doi.org/10.1080/19392397.2016.1218292
Knapp RH (1944) A psychology of rumor. Public Opin Q 8(1):22–37. https://doi.org/10.1086/265665
Lee H, Oh HJ (2017) Normative mechanism of rumor dissemination on Twitter. Cyberpsychology Behav Soc Netw 20(3):164–171. https://doi.org/10.1089/cyber.2016.0447
Li M, Liu F (2016) Game theory-based network rumor spreading model. In: 2016 International Conference on Network and Information Systems for Computers (ICNISC), IEEE, pp 89–94, https://doi.org/10.1109/ICNISC.2016.029
Li Y, Ma J, Fang F (2020) How the emotion’s type and intensity affect rumor spreading. arXiv preprint https://doi.org/10.48550/arXiv.2012.08861
Liu W, Wu X, Yang W, Zhu X, Zhong S (2019) Modeling cyber rumor spreading over mobile social networks: A compartment approach. Appl Math Comput 343:214–229. https://doi.org/10.1016/j.amc.2018.09.048
Lu F, Zhang W, Shao L, Jiang X, Xu P, Jin H (2017) Scalable influence maximization under independent cascade model. J Netw Comput Appl 86:15–23. https://doi.org/10.1016/j.jnca.2016.10.020
Lu L, Ouyang Y (2019) Dynamic vaccination game in a heterogeneous mixing population. Phys A 533:122032. https://doi.org/10.1016/j.physa.2019.122032
Lü L, Chen DB, Zhou T (2011) The small world yields the most effective information spreading. New J Phys 13(12):123005. https://doi.org/10.1088/1367-2630/13/12/123005
Maki DP, Thompson M (1973) Mathematical models and applications: with emphasis on the social life, and management sciences. Tech. rep
Mashwama P, Fashoto SG, Mbunge E, Gwebu S (2020) Development of a mobile inter-vehicular communication system based on gossip algorithm. Int J Interact Mob Technol 14(11). https://doi.org/10.3991/ijim.v14i11.12949
McDougall J, Stoner EC (1938) The computation of Fermi-Dirac functions. Proc R Soc Lond A 237(773):67–104. https://doi.org/10.1098/rsta.1938.0004
Miller JC (2011) A note on a paper by Erik Volz: SIR dynamics in random networks. J Math Biol 62(3):349–358. https://doi.org/10.1007/s00285-010-0337-9
Molloy M, Reed B (1995) A critical point for random graphs with a given degree sequence. Random Struct Algorithms 6(2–3):161–180. https://doi.org/10.1002/rsa.3240060204
Muhlmeyer M, Agarwal S, Huang J (2020) Modeling social contagion and information diffusion in complex socio-technical systems. IEEE Syst J 14(4):5187–5198. https://doi.org/10.1109/JSYST.2020.2993542
Nekovee M, Moreno Y, Bianconi G, Marsili M (2007) Theory of rumour spreading in complex social networks. Phys A 374(1):457–470. https://doi.org/10.1016/j.physa.2006.07.017
Newman ME, Strogatz SH, Watts DJ (2001) Random graphs with arbitrary degree distributions and their applications. Phys Rev E 64(2):026118. https://doi.org/10.1103/PhysRevE.64.026118
Pratt JW (1978) Risk aversion in the small and in the large. In: Uncertainty in economics, Elsevier, pp 59–79, https://doi.org/10.1016/B978-0-12-214850-7.50010-3
Qing D, ZhengGong Z (2020) A stochastic game model for analysis of rumor and anti-rumor propagation in social networks. In: 2020 IEEE 6th International Conference on Control Science and Systems Engineering (ICCSSE), IEEE, pp 63–67, https://doi.org/10.1109/ICCSSE50399.2020.9171954
Rey D, Gardner L, Waller ST (2016) Finding outbreak trees in networks with limited information. Netw Spat Econ 16(2):687–721. https://doi.org/10.1007/s11067-015-9294-6
Spencer S, Srikant R (2015) On the impossibility of localizing multiple rumor sources in a line graph. ACM SIGMETRICS Performance Evaluation Review 43(2):66–68. https://doi.org/10.1145/2825236.2825262
Sudbury A (1985) The proportion of the population never hearing a rumour. J Appl Probab 22(2):443–446. https://doi.org/10.2307/3213787
Vega-Oliveros DA, da Fontoura Costa L, Rodrigues FA (2020) Influence maximization by rumor spreading on correlated networks through community identification. Commun Nonlinear Sci Numer Simul 83:105094. https://doi.org/10.1016/j.cnsns.2019.105094
Volz E (2008) SIR dynamics in random networks with heterogeneous connectivity. J Math Biol 56(3):293–310. https://doi.org/10.1007/s00285-007-0116-4
Wang B, Chen G, Fu L, Song L, Wang X (2017) Drimux: Dynamic rumor influence minimization with user experience in social networks. IEEE Trans Knowl Data Eng 29(10):2168–2181. https://doi.org/10.1109/TKDE.2017.2728064
Wang Y, Wu J, Yang WS (2013) Cloud-based multicasting with feedback in mobile social networks. IEEE Trans Wirel Commun 12(12):6043–6053. https://doi.org/10.1109/TWC.2013.102313.121508
Wang Y, Chen X, Li J (2015) A new genetic-based rumor diffusion model for social networks. In: 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC), IEEE, pp 1–5, https://doi.org/10.1109/SSIC.2015.7245327
Xian J, Yang D, Pan L, Liu M (2020) Wang W (2020) Containing rumors spreading on correlated multiplex networks. J Stat Mech-Theory Exp 2:023402. https://doi.org/10.1088/1742-5468/ab6849
Xiang N, Zhou Z, Pan Z (2018) Using SIR model to simulate emotion contagion in dynamic crowd aggregation process. Int J Performability Eng 14(1):134, https://doi.org/10.23940/ijpe.18.01.p14.134143
Xiao Y, Chen D, Wei S, Li Q, Wang H, Xu M (2019) Rumor propagation dynamic model based on evolutionary game and anti-rumor. Nonlinear Dyn 95(1):523–539. https://doi.org/10.1007/s11071-018-4579-1
Yan X, Jiang P (2018) Effect of the dynamics of human behavior on the competitive spreading of information. Comput Hum Behav 89:1–7. https://doi.org/10.1016/j.chb.2018.07.014
Zan Y (2018) DSIR double-rumors spreading model in complex networks. Chaos, Solitons & Fractals 110:191–202. https://doi.org/10.1016/j.chaos.2018.03.021
Zan Y, Wu J, Li P, Yu Q (2014) SICR rumor spreading model in complex networks: Counterattack and self-resistance. Phys A 405:159–170. https://doi.org/10.1016/j.physa.2014.03.021
Zanette DH (2002) Dynamics of rumor propagation on small-world networks. Phys Rev E 65(4):041908. https://doi.org/10.1103/PhysRevE.65.041908
Zhang Y, Su Y, Li W, Liu H (2018) Modeling rumor propagation and refutation with time effect in online social networks. Int J Mod Phys C 29(08):1850068. https://doi.org/10.1142/S0129183118500687
Zhu T, Wang B, Wu B, Zhu C (2014) Maximizing the spread of influence ranking in social networks. Inf Sci 278:535–544. https://doi.org/10.1016/j.ins.2014.03.070
Zhuang YB, Chen J, Li Zh (2017) Modeling the cooperative and competitive contagions in online social networks. Phys A 484:141–151. https://doi.org/10.1016/j.physa.2017.04.129
Zinoviev D, Duong V (2011) A game theoretical approach to broadcast information diffusion in social networks. arXiv preprint arXiv:11065174 https://doi.org/10.48550/arXiv.1106.5174730
Acknowledgements
The authors thank the editor and two anonymous referees for their valuable suggestions. The first author was a visiting doctoral student at Illinois while this research was conducted. The first author also thanks Mr. Ruifeng She (Ph.D. student at Illinois) for his comments and help.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing Interests
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix A. Derivation of \(R_e\)
Appendix A. Derivation of \(R_e\)
We follow the idea mentioned in Diekmann et al. (1990) to derive \(R_e(t)\) which the definition can be found in Sect. 3.2. The computation of \(R_e(t)\) requires information only on compartments \(H_{jk}(t)\), \(I_{jk}(t)\) and \(M_{jk}(t)\). For simplicity, we hereon omit the time argument for all variables in this appendix.
Based on Eq. (18), for all \(j \in \{1, ...,J\}, k \in \{1, ...,K\}\), we have
This can be written in the following vector form
where \(\mathcal {F} = [1 \cdot (r_I \frac{\theta _I}{\theta } + r_M \frac{\theta _M}{\theta })S_{11}, \cdots , J(r_I\frac{\theta _I}{\theta } + r_M\frac{\theta _M}{\theta })S_{JK}, \mathbf {0}_{1 \times JK}, \mathbf {0}_{1 \times JK}]^T\) represents the increment of hesitating users from all other compartments, while \(\begin{aligned}&\mathcal {V} = [\beta H_{11}, \cdots , \beta H_{JK}, \mu _{I}I_{11}-\beta \gamma _{11} q H_{11}, \cdots , \mu _{I}I_{JK}-\beta \gamma _{JK}qH_{JK}, \mu _{M}M_{11}-\beta \gamma _{11}(1 - q)H_{11}, \cdots , \mu _{M}M_{JK}-\beta \gamma _{JK}(1 - q)H_{JK}]^T\end{aligned}\) represents the transmission of hesitating users into other compartments. Here \(\mathbf {0}\) represents a zero vector/matrix. The Jacobian matrices of \(\mathcal {F}\) and \(\mathcal {V}\), denoted as F and V, can be computed respectively as follows:
where
In the above, E represents the identity matrix. Following Diekmann et al. (1990), we call \(FV^{-1}\) the next generation matrix for the model, and it can be calculated as:
It is well known from Lyapunov stability theorem that the effective reproduction number \(R_e\) is the spectral radius of matrix \(FV^{-1}\); i.e.:
From Eq. (29), \(FV^{-1}\) is an upper triangular block matrix, whose eigenvalues are given by those of its only nonzero diagonal block submatrix \(-BQ^{-1}PD^{-1}\). Note that
Clearly, rank (\(-BQ^{-1}PD^{-1}\)) = 1. Hence,
Rights and permissions
About this article
Cite this article
Liu, W., Wang, J. & Ouyang, Y. Rumor Transmission in Online Social Networks Under Nash Equilibrium of a Psychological Decision Game. Netw Spat Econ 22, 831–854 (2022). https://doi.org/10.1007/s11067-022-09574-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11067-022-09574-9