Abstract
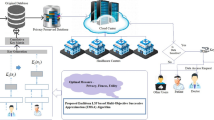
Cloud computing is now used by many enterprises due to its increased computational efficiency, economic effectiveness, as well as flexibility. However, security is currently the main issue impeding the cloud computing platform's growth. Therefore, Decentralized Information Flow Control (DIFC) has been proposed as a suitable remedy for resolving the cloud security problems. Using conventional network access and encryption technology was not practicable in the DIFC to effectively restrict the spread of the tenant's personal data inside the system. Therefore, a novel DIFC framework for cloud virtual machines (VM) is suggested here. The suggested system encapsulates four entities such as central authority (CA), encryption proxy (EP), cloud server (CS), and cloud tenant VM. The EP has implemented the ciphertext data-flow security technique. Encryption is carried out using the newly proposed hybrid “Advanced Encryption Standard (AES)–Elliptic Curve Cryptography (ECC) algorithm”. The hybrid AES-ECC encryption technique uses the proposed Improved Poor Rich Optimization (IPRO) model to compute the optimal key. The implementation of the developed work is evaluated against the existing works for the "Chess, T1014D100K, and Retail datasets”. In particular, for the T1014D100K dataset, the cost function of the suggested model at the 2.5th iteration is 57.14%, 62.05%, 80%, 54.2%, and 56% better than the old models like BOA, SMO, SSA, PRO, and LA correspondingly.













Similar content being viewed by others
Data availability
The dataset used for this work are Chess, T1014D100K, and retail dataset.
Abbreviations
- AES:
-
Advanced encryption standard
- AOPF-SFS:
-
Attribute-order-preserving-free-SFS
- AT-DIFC+:
-
Adaptive trust-aware decentralized information flow control
- BFA:
-
Brute force attack
- BOA:
-
Butterfly optimization algorithm
- CA:
-
Central authority
- CS:
-
Cloud server
- DIFC:
-
Decentralized information flow control
- ECC:
-
Elliptic curve cryptography
- EP:
-
Encryption proxy
- IFC:
-
Information flow control
- IPRO:
-
Improved poor rich optimization algorithm
- KPA:
-
Known-plaintext attack
- LA:
-
Lion algorithm
- OBL:
-
Opposition based learning
- PRO:
-
Poor rich optimization algorithm
- RSA:
-
Rivest–Shamir–Adleman cryptosystem
- SFS:
-
Sort-filter-skyline
- SMO:
-
Spider monkey optimization
- VM:
-
Virtual machines
- SSA:
-
Salp Swarm algorithm
- TLC-IFC:
-
Tenant-led ciphertext information flow control
References
Ali, R., Ak, P.: A secure three-factor remote user authentication scheme using elliptic curve cryptosystem. In: Proceedings of the international conference on microelectronics, Computing and communication systems, pp. 9–24. Springer, Singapore (2018a)
Ali, R., Pal, A.K.: An efficient three factor–based authentication scheme in multiserver environment using ECC. Int. J. Commun. Syst. 31(4), e3484 (2018b)
Alqahtani, F., Salahaldeen, D., Predrag, T.T., Frederick, T.S.: Information flow control to secure data in the cloud. In: International Conference on Computational Science and Computational Intelligence (CSCI) (2020)
Anandkumar, R., Kalpana, R.: A review on chaos-based image encryption using fractal function. Exam Fractal Image Process. Anal. 23–37 (2020)
Anandkumar, R., Kalpana, R.: A Fibonacci p-code traversing and unified chaotic map-based image encryption algorithm. J. Ambient. Intell. Humaniz. Comput. 13, 3713–3727 (2022)
Anandkumar, R., Dinesh, K., Obaid, A.J., Malik, P., Sharma, R., Dumka, A., Singh, R., Khatak, S.: Securing e-Health application of cloud computing using hyperchaotic image encryption framework. Comput. Electr. Eng. 100, 107860 (2022)
Bauereiß, T., Gritti, A.P., Popescu, A., Raimondi, F.: CoSMeDis: a distributed social media platform with formally verified confidentiality guarantees. IEEE Symp. Secur. Privacy (SP) (2017). https://doi.org/10.1109/SP.2017.24
Bhagyashri, A., Gurav, Y.B.: Privacy-preserving public auditing for secure cloud storage. IOSR J. Comput. Eng. (2014). https://doi.org/10.1109/TC.2011.245
Bhuarya, P., Chandrakar, P., Ali, R., Sharaff, A.: An enhanced authentication scheme for Internet of Things and cloud based on elliptic curve cryptography. Int. J. Commun. Syst. 34(10), e4834 (2021)
Bolodurina, I., Parfenov, D., Shukhman, A.: Approach to the effective controlling cloud computing resources in data centers for providing multimedia services. Int. Sib. Conf. Control Commun. (SIBCON) (2015). https://doi.org/10.1109/SIBCON.2015.7147170
Candotti, D., Steel, M.D.W., West, A.C.: Charting the course for Tasmania’s energy cloud roadmap IEEE PES Asia-Pacific power and energy engineering conference (APPEEC). IEEE PES Asia-Pacific Power Energy Eng. Conf. (APPEEC) (2015). https://doi.org/10.1109/APPEEC.2015.7380915
Cuzzocrea, A., Panagiotis, K., Akrivi, V.: Effective and efficient skyline query processing over attribute-order-preserving-free encrypted data in cloud-enabled databases. Future Gener. Comput. Syst. 126, 237–251 (2022)
Hamid, S., Moosavi, S.H., Bardsiri, V.K.: Poor and rich optimization algorithm: a new human-based and multi populations algorithm. Eng. Appl. Artif. Intell. 86, 165–181 (2019)
Khurshid, A., Khan, A.N., Khan, F.G., Ali, M., Shuja, J., Khan, A.U.: Secure-CamFlow: a device-oriented security model to assist information flow control systems in cloud environments for IoTs. Concurr. Comput. 31(8), e4729 (2019)
Khan, M.A., Quasim, M.T., Alghamdi, N.S., Khan, M.Y.: A secure framework for authentication and encryption using improved ECC for IoT-based medical sensor data. IEEE Access 8, 52018–52027 (2020). https://doi.org/10.1109/ACCESS.2020.2980739
Mane, P.S., Gurav, Y.B.: A survey on information flow control for secure cloud computing. Int. J. Innov. Res. Comput. Commun. Eng 11, 76–89 (2015)
Mane, P.S., Gurav, Y.B.: Secure cloud computing using decentralized information flow control. Int. Adv. Res. J. Sci. Eng. Technol 3, 167–170 (2016)
Naeem, H.: Detection of malicious activities in internet of things environment based on binary visualization and machine intelligence. Wirel. Pers. Commun. 108, 2609–2629 (2019)
Pasquier, T.F.J., Powles, J.E.: Expressing and enforcing location requirements in the cloud using information flow control. IEEE Int. Conf. Cloud Eng. (2015). https://doi.org/10.1109/IC2E.2015.71
Pasquier, T.F.J., Singh, J., Eyers, D., Bacon, J.: Camflow: managed data-sharing for cloud services. IEEE Trans. Cloud Comput. 5(3), 472–484 (2017). https://doi.org/10.1109/TCC.2015.2489211
Pasquier, T.F.J., Singh, J., Bacon, J., Eyers, D.: Information flow audit for PaaS clouds. IEEE Int. Conf. Cloud Eng. (ICE) (2019). https://doi.org/10.1109/IC2E.2016.19
Patra, S., Kalapureddy, M.C.R.: Cloud radar observations of multi-scale variability of cloud vertical structure associated with Indian summer monsoon over a tropical location. Clim. Dyn. 56, 1055–1081 (2021)
Phatak, A., Kadikar, R., Vijayan, K., Amutha, B.: Performance analysis of firewall based on SDN and open flow. Int. Conf. Commun. Signal. Process. (ICCSP) (2018). https://doi.org/10.1109/ICCSP.2018.8524164
Shahidinejad, A., Ghobaei-Arani, M., Esmaeili, L.: An elastic controller using colored petri nets in cloud computing environment. Clust. Comput. 23, 1045–1071 (2020)
Shrinath, A.K.: Information flow control for secure cloud computing. Imp. J. Interdiscip. Res. (2017). https://doi.org/10.1109/TNSM.2013.122313.130423
Skandylas, C., Khakpour, N., Andersson, J.: AT-DIFC+: toward adaptive and trust-aware decentralized information flow control. ACM Trans. Auton. Adapt. Syst. (TAAS) 15(4), 1–35 (2021)
Solanki, N., Zhu, W., Yen, I., Bastani, F., Rezvani, E.: Multi-tenant access and information flow control for SaaS. IEEE Int. Conf. Web Serv. (ICWS) (2016). https://doi.org/10.1109/ICWS.2016.21
Somavanshi, N.R., Gurav, Y.B.: Survey of decentralized information flow controlfor relational database-IFDB. Int. J. Eng. Res. Ind. Appl 8, 27–36 (2015)
Somavanshi, N.R., Gurav, Y.B.: Security in cloud computing environment by decentralized information flow control. Int. J. Innov. Res. Comput. Commun. Eng 4(6), 1–3 (2016)
Xi, N., Ma, J., Sun, C., Di, Lu., Shen, Y.: Information flow control on encrypted data for service composition among multiple clouds. Distrib. Parallel Databases 36, 511–527 (2019)
Zaw, T.M., Thant, M., Bezzateev, S.V.: Database security with AES encryption, elliptic curve encryption and signature. Wave Electr. Appl. Inf. Telecommun. Syst. (WECONF) (2019). https://doi.org/10.1109/WECONF.2019.8840125
Zhang, Z., Zhi, Y., Xuehui, D., Wenfa, L., Xingyuan, C., Lei, S.: Tenant-led ciphertext information flow control for cloud virtual machines. IEEE Access (2020). https://doi.org/10.1109/ACCESS.2021.3051061
Zhou, L., Zhang, H., Zhang, K., Wang, B., Shen, D., Wang, Y.: Advances in applying cloud computing techniques for air traffic systems. IEEE Int. Conf. Civil Aviat. Saf. Inf. Technol. (2020). https://doi.org/10.1109/ICCASIT50869.2020.9368768
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gurav, Y.B., Patil, B.M. De-centralized information flow control for cloud virtual machines with hybrid AES-ECC and improved meta-heuristic optimization based optimal key generation. Int J Intell Robot Appl 7, 406–425 (2023). https://doi.org/10.1007/s41315-022-00268-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41315-022-00268-6