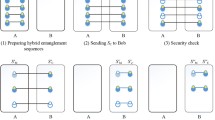
Abstract
For the strategy of expanding dense coding protocols, firstly, a high-dimensional Hadamard matrix and CNOT gate are designed, and the encryption and decryption processes are implemented. Secondly, extend the protocol to multiple parties and consider attempting to establish an objective function for success probability when the initial resource is not the maximum quantum entangled state. Finally, we reconstruct the encryption and decryption processes in non-maximally entangled GHZ states. The research shows that this group of protocols is theoretically feasible in the infinite dimensional space, and confirms the advantages of high-dimensional entanglement, such as high channel capacity and strong anti-eavesdropping ability, which provides a good theoretical basis for in-depth research of high-dimensional entanglement in the field of quantum information.




Similar content being viewed by others
Data availability
The data used to support the findings of this study are included within the article.
Change history
25 March 2024
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s10878-024-01139-5
References
Ban M, Kitajima S, Shibata F (2004) The classical capacity of a quantum dense coding system. J Phys A Math Gen A Europhys J 37(35):429–434
Barenco A, Bennett CH, Cleve R, Divincenzo DP, Margolus N, Shor P, Sleator T, Smolin J, Weinfurter H (1995) Elementary gates for quantum computation. Phys Rev A Atomic Mol Opt Phys 52(5):3457–3467
Bennett CH, Brassard G (1989) Experimental quantum cryptography: the dawn of a new era for quantum cryptography: the experimental prototype is working. ACM SIGACT News 20(4):78–80
Bennett CH, Wiesner SJ (1992) Communication via one- and two-particle operators on Einstein-Podolsky-Rosen states. Phys Rev Lett 69(20):2881–2884
Bennett CH, Bessette F, Brassard G, Salvail L, Smolin J (1991) Experimental quantum cryptography. Lect Notes Comput Sci 473(1):253–265
Bose S, Vedral V, Knight PL (1998) Multiparticle generalization of entanglement swapping. Phys Rev A 57(2):822–829
Bose S, Plenio MB, Vedral V (2000) Mixed state dense coding and its relation to entanglement measures. J Mod Opt 47(2–3):291–310
Cao ZW, Feng XY, Kang WH, Luo R, Jiang EC (2012) Quantum secure direct communication based on quantum dense coding using a class of w-states. J Optoelectron Laser 23(6):1152–1158
Chen XY, Li X, Jia XF, Yang GH (2006) Entanglement enhanced information transmission of a Pauli memory channel. Phys Lett A 361(1):43–47
Datta N, Leditzky F (2015) Second-order asymptotics for source coding, dense coding, and pure-state entanglement conversions. IEEE Trans Inf Theory 61(1):582–608
Deng FG, Long GL, Liu XS (2003) Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys Rev A 68(4):113–114
Devetak I, Shor PW (2005) The capacity of a quantum channel for simultaneous transmission of classical and quantum information. Commun Math Phys 256(2):287–303
Feynman RP (1982) Simulating physics with computers. Int J Theor Phys 21(6–7):467–488
Hu TT, Xue K, Sun CF, Wang GC, Ren H (2013) Quantum teleportation and dense coding via topological basis. Quantum Inf Process 12(11):3369–3381
Hu XM, Guo Y, Liu BH, Huang YF, Li CF, Guo GC (2018) Beating the channel capacity limit for superdense coding with entangled ququarts. Sci Adv 4(7):eaat9304
Ingraham MH, Wegner KW (1935) The equivalence of pairs of Hermitian matrices. AMS 38(1):145–162
Kim IH (2007) Quantumness, generalized 2-desing and symmetric informationally complete POVM. Quantum Inf Comput 7(8):730–737
Krister S (2022) Quantum entanglement provides a key to improved security. Nature 607(7920):662–664
Kyota F, Akira S (2016) Universal property of quantum measurements of equilibrium fluctuations and violation of the fluctuation-dissipation theorem. Phys Rev Lett 117(1):010402
Lee HC (1948) Canonical factorization of pseudo-unitary matrices. Proc London Math Soc s2-50(1):230–241
Lee HJ, Ahn D, Hwang SW (2002) Dense coding in entangled states. Phys Rev A 66(2):024304
Liao XP, Fang MF, Chen XM, Cai JW, Zheng XJ (2005) Quantum entanglement in a system of two spatially separated atoms driven by an external coherent laser field. J Opt B: Quantum Semiclassical Opt 7(11):323
Ma HY, Ma YL, Zhang WB, Zhao XL, Chu PC (2021) Development of video encryption scheme based on quantum controlled dense coding using GHZ state for smart home scenario. Wirel Pers Commun 123(1):295–309
Mattle K, Weinfurter H, Kwiat PG, Zeilinger A (1996) Dense coding in experimental quantum communication. Phys Rev Lett 76(25):4656–4659
Miltersen PB, Nisan N, Safraa S, Wigderson A (1998) On data structures and asymmetric communication complexity. J Comput Syst Sci 57(1):37–49
Paraso TK, Roger T, Marangon DG, Marco ID, Sanzaro M, Woodward RI, Dynes JF, Yuan Z, Shields AJ (2021) A photonic integrated quantum secure communication system. Nat Photonics 15(11):850–856
Patera J, Zassenhaus H (1988) The pauli matrices in n dimensions and finest gradings of simple lie algebras of type An −1. J Math Phys 29(3):665–673
Richardson AR (1936) Conjugate Matrices. Q J Math os-7(1):256–270
Shevchenko V, Bravina L, Foka Y, Kabana S (2015) Quantum measurements and Landauer’s principle. EPJ Web Conf 95:03034
Skotiniotis M, Dür W, Kraus B (2013) Efficient quantum communication under collective noise. Quantum Inf Comput 13(3–4):290–323
Wang C, Deng FG, Li YS, Liu XS, Long GL (2005) Quantum secure direct communication with high-dimension quantum superdense coding. Phys Rev A 71(4):43051–43054
Weichsel PM (1962) The kronecker product of graphs. Proc Am Math Soc 13(1):47–52
Ye L, Yu LB (2005) Scheme for implementing quantum dense coding using tripartite entanglement in cavity QED. Phys Lett A 346(5):330–336
Yinnon H, Uhlmann DR (1983) Applications of thermoanalytical techniques to the study of crystallization kinetics in glass-forming liquids, part I: theory. J Non-Cryst Solids 54(3):253–275
Zhao X, Li YQ, Cheng LY, Yang GH (2019) The quantum dense coding in a two atomic system under the non-markovian environment. Int J Theor Phys 58(2):493–501
Funding
The authors have not disclosed any funding.
Author information
Authors and Affiliations
Contributions
SKX was responsible for the methodology; conceptualization; supervision and leadership. MJZ contributed to the verification, review, and editing. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there are no conflicts of interest regarding the publication of this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail: https://doi.org/10.1007/s10878-024-01139-5
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Xia, SK., Zeng, MJ. RETRACTED ARTICLE: Design of extended dense coding protocol strategy based on combinatorial optimization. J Comb Optim 45, 133 (2023). https://doi.org/10.1007/s10878-023-01060-3
Accepted:
Published:
DOI: https://doi.org/10.1007/s10878-023-01060-3