Abstract
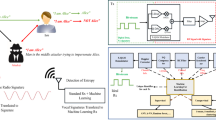
This paper concentrate on an option for mitigating distributed denial of service (DDoS) attacks that can stern consequences in mobile ad hoc network (MANET). Discovering a solution to a DDoS attack has gained research focus but challenges exists in performing attack detection with high accuracy along with developing a mechanism in detecting diverse methods to classify DDoS attack activities and also to classify it as an effective measure. The existing methods have numerous difficulties involving detection system performance limits, system scalability and stability, and the capability to develop large volumes of information. This paper concentrates on ETC with randomized search algorithm to detect attacks categorized as flooding, scheduling, black holes and gray holes, using a machine learning (ML) technique as classifier for understanding the behavior of these attacks and trains the better classification method in the MANET data transmitting dataset. The ETC algorithm employs the traditional top-down construction method to construct an ensemble of unpruned decision or regression trees. It separates nodes by selecting cut points thresholds completely at random, which sets it apart from previous tree-based ensemble approaches. When the data transmitted in the AODV, the behavior of node is analyzed and reported in the dataset as target which is trained through ML method. This AODV with ML proposed model can justify the behavior of network in MANET and classify the attack type for the current application. Moreover, the ML method performance has been developed through hyperparameter tuning which can be evaluated through confusion matrix metrics. This AODV with extra tree classifier (ETC) generate improved accuracy as 98.89% using hyperparameter tuning process in determining the safe data transaction in MANET.












Similar content being viewed by others
Data Availability
The data and source codes used to support the findings of this study can be obtained from the corresponding author upon request.
References
Abdelshafy MA, King PJB (2016) Resisting blackhole attacks on MANETs. In: Proc 13th IEEE Annu Consum Commun Netw Conf (CCNC), Las Vegas, NV, USA, pp. 1048–1053
Adumbabu I, Selvakumar K (2022) Hybrid link states predicting model for cluster head selection and its routing analysis for WSN MANETS. In: 2022 International conference on electronics and renewable systems (ICEARS), Tuticorin, India, pp. 670–677
Agarkar PT, Chawhan MD, Kulat KD, Hajare PR (2022) Zone based selective neighbours to mitigate flooding & reliable routing for WSN. In: 2022 International conference on connected systems & intelligence (CSI), Trivandrum, India, 2022, pp. 1–7
Ahmed AJ, Rashid SA, Hamdi MM, Mustafa AS, Noori MS (2022) A review of wireless sensor network. In: 2022 international congress on human-computer interaction, optimization and robotic applications (HORA), Ankara, Turkey, pp. 1–5
Ananthalakshmi G, Ravindra T (2022) Design and analysis Of EE-LEACH routing protocols in MANET for wireless sensor network. In: 2022 3rd international conference for emerging technology (INCET), Belgaum, India, pp. 1–4
Ardianto B, Dwi Nurcahyo HS, Muftić H, Harwahyu R, Sari RF (2022) Performance comparison of AODV, AODV-ETX and modified AODV-ETX in VANET using NS3. In: 2022 IEEE international conference on cybernetics and computational intelligence (CyberneticsCom), Malang, Indonesia, pp. 156–161
Bruzgiene R, Narbutaite L, Adomkus T (2017) MANET network in Internet of Things system. In: Ortiz JH, de la Cruz AP (eds) Ad Hoc networks. InTech, Rijeka
Daou L, Rafla N (2019) Analysis of black hole router attack in network-on-chip. In: Midwest Symp Circuits Syst, pp. 69–72
El-Semary AM, Diab H (2019) BP-AODV: blackhole protected AODV routing protocol for MANETs based on chaotic map. IEEE Access 7:95197–95211
Faghihniya MJ, Hosseini SM, Tahmasebi M (2017) ‘Security upgrade against RREQ flooding attack by using balance index on vehicular ad hoc network.’ Wireless Netw 23(6):1863–1874
Gao Y, Wu H, Song B, Jin Y, Luo X, Zeng X (2019) A distributed network intrusion detection system for distributed denial of service attacks in vehicular ad hoc network. IEEE Access 7:154560–154571
Gul H, Bin Ahmad M, Asif M (2019) A comparison of detection techniques for attacks on MANETs. In: Proc - 2019 4th Int Conf Inf Syst Eng ICISE, 2019, pp. 81–86
Gurulakshmi K, Nesarani A (2018) Analysis of IoT bots against DDoS attack using machine learning algorithm. In: Proc 2nd Int Conf Trends Electron Inform (ICOEI), pp. 1052–1057
Hmeidi I, Khamayseh Y, Al-Rousen M, Arrabi A (2018) Blackhole attack security issues, challenges and solution in manet. In: Dhinaharan Nagamalai et al. (Eds) CSEIT, NCS, SPM, NeTCoM - 2018 pp. 199–207, 2018. © CS & IT-CSCP
Jain AK, Choorasiya A (2017) Security enhancement of AODV routing protocol in mobile ad hoc network. In: Proc 2nd Int Conf Commun Electron Syst. (ICCES), Coimbatore, India, pp. 958–964
Kaur H, Mangat K (2017) Black hole attack in mobile ad hoc networks: a review. Int J Adv Res Ideas Innov Technol 3(2):189–191
Khanna N, Sachdeva M (2019) A comprehensive taxonomy of schemes to detect and mitigate blackhole attack and its variants in MANETs. Comput Sci Rev 32:24–44
Ling C, Sun WS (2019) Wireless Sensor networks routing based on improved ant colony algorithm. Comput Eng Design 40(3):627–631
Ochola EO, Mejaele LF, Eloff MM, van der Poll JA (2017) Manet reactive routing protocols node mobility variation effect in analyzing the impact of black hole attack. SAIEE Afr Res J 108(2):80–92
Pandey S, Singh V (2020) Blackhole attack detection using machine learning approach on MANET. In: 2020 international conference on electronics and sustainable communication systems (ICESC), Coimbatore, India, pp. 797–802
Panos C, Ntantogian C, Malliaros S, Xenakis C (2017) Analyzing, quantifying, and detecting the blackhole attack in infrastructure-less networks’. Comput Netw 113:94–110
Praveen KS, Gururaj HL, Ramesh B (2016) Comparative analysis of black hole attack in ad hoc network using AODV and OLSR protocols. Proc Comput Sci 85:325–330
Saied A, Overill RE, Radzik T (2016) Detection of known and unknown DDoS attacks using artificial neural networks. Neurocomputing 172:385–393
Singh U, Shukla M, Jain AK, Patsariya M, Itare R, Yadav S (2020) Trust based model for mobile ad-hoc network in Internet of Things. Invent Comput Technol 4:827–839
Trivedi MC, Yadav S, Singh VK (2019) Securing ZRP routing protocol against DDoS attack in mobile ad hoc network. In: Kolhe ML, Trivedi MC, Tiwari S, Singh VK (eds) Advances in data and information sciences (Lecture Notes in Networks and Systems). Springer, Singapore, pp 387–396
Wang M, Wang X, Zhang Y, Gao Z (2018) ‘A novel chaotic encryption scheme based on image segmentation and multiple diffusion models.’ Opt Laser Technol 108:558–573
Xu J (2021) A modified AODV routing protocol using in WSN based on ant colony algorithm. In: 2021 2nd international conference on electronics, communications and information technology (CECIT), Sanya, China, pp. 87–90
Yasin A, Zant MA (2018) Detecting and isolating black-hole attacks in MANET using timer based baited technique. Wirel Commun Mobile Comput 2018:9812135
Ye Y, Feng S, Liu M, Sun X, Xu T, Ting X (2018) A safe proactive routing protocol SDSDV for ad hoc network. Int J Wirel Inf Netw 25(3):348–357
Yuan X, Li C, Li X (2017) DeepDefense: identifying DDoS attack via deep learning. In: Proc IEEE Int Conf Smart Comput, pp. 1–8
Zekri M, El Kafhali S, Aboutabit N, Saadi Y (2017) DDoS attack detection using machine learning techniques in cloud computing environments. In: Proc 3rd Int Conf Cloud Comput Technol Appl (CloudTech), pp. 1–7
Zhang B, Zhang T, Yu Z (2017) DDoS detection and prevention based on artificial intelligence techniques. In: Proc 3rd IEEE Int Conf Comput Commun (ICCC), pp. 1276–1280
Funding
The authors have not received any funding for the work presented in the paper.
Author information
Authors and Affiliations
Contributions
NS involved in data collection and analysis, methodology, original draft, and validation. AR involved in corrections/revision of manuscript and validation. SA involved in methodology and validation. KSA involved in report writing and data analysis.
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no competing interests.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sivanesan, N., Rajesh, A., Anitha, S. et al. Detecting Distributed Denial of Service (DDoS) in MANET Using Ad Hoc On-Demand Distance Vector (AODV) with Extra Tree Classifier (ETC). Iran J Sci Technol Trans Electr Eng (2023). https://doi.org/10.1007/s40998-023-00678-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s40998-023-00678-7