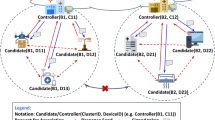
Abstract
With the popularity of the Internet of Things (IoT), massive amounts of data are generated every second. By analyzing this data, attackers can launch kinds of attacks for their own profits, such as data tampering, malicious data injection, identity deception etc. To solve these problems, in this paper, we propose a Trusted Execution Environment-and-Blockchain-based data protection architecture (TEDA). In TEDA, edge devices in different IoTs maintain a consortium blockchain to achieve the secure read/write operations and verification of data together with cloud. Besides, to secure the local data processing in edge devices and manage internal light-weight devices, an Intel SGX-based module is designed. Furthermore, a new transaction structure is introduced to protect user’s access pattern. The experimental results show that the space occupancy rates of write and read of TEDA with SGX are 0.84\(\times \) and 1.07\(\times \) than that of TEDA without SGX, and the time occupancy rates of write and read of TEDA with SGX are 0.94\(\times \) and 0.90\(\times \) than that of TEDA without SGX, which indicate TEDA has a good performance.








Similar content being viewed by others
References
He W, Golla M, Padhi R, Ofek J, Durmuth M, Fernandes E, Ur B (2018) Rethinking access control and authentication for the home internet of things (iot). USENIX, 255–272
Zhang S, Rong J, Wang B (2020) A privacy protection scheme of smart meter for decentralized smart home environment based on consortium blockchain. Electr Power Energy Syste 1–10
Zhang B, Mor N, Kolb J, Chan DS, Goyal N (2015) The cloud is not enough: saving iot from the cloud. In: Proceedings of the 7th USENIX Conference on Hot Topics in Cloud ComputingJuly
Orenbach M, Lifshits P, Minkin M, Silberstein M (2017) Eleos: exitless os services for sgx enclaves. The Twelfth European Conference, pp 238–253
Arnautov S, Trach B, Gregor F, Knauth T, Martin A, Priebe C, Lind J, Muthukumaran D, O’Keeffe D, Stillwell ML, Goltzsche D, Eyers D, Kapitza R, Pietzuch P, Fetzer C (2016) Scone: secure linux containers with intel sgx. USENIX, pp 689–703
Kim T, Park J, Woo J, Jeon S, Huh J (2019) Shieldstore: shielded in-memory key-value storage with sgx. In: Proceedings of the 14th EuroSys Conference 2019
Bailleu M, Thalheim J, Bhatotia P, Fetzer C, Honda M, Vaswani K (2019) Speicher: securing lsm-based key-value stores using shielded execution. In: 17th USENIX Conference on File and Storage Technologies (FAST ’19), pp 173–190
Shen M, Liu H, Zhu L, Xu K, Yu H, Du X, Guizani M (2020) Blockchain-assisted secure device authentication for cross-domain industrial iot. IEEE J Sel Areas Commun 942–954
Hu Y, Kumar S, Popa RA (2020) Ghostor: toward a secure data-sharing system from decentralized trust. In: 17th USENIX symposium on networked systems design and implementation (NSDI ’20), pp 851–877
Jangirala S, Das AK, Vasilakos AV (2019) Designing secure lightweight blockchain-enabled rfid-based authentication protocol for supply chains in 5g mobile edge computing environment. IEEE Trans Ind Inform 1–13
Yang H, Liang Y, Yuan J, Yao Q, Yu A, Zhang J (2020) Distributed blockchain-based trusted multi-domain collaboration for mobile edge computing in 5g and beyond. IEEE Trans Ind Inform 7094–7104
Chen Y, Xie H, Lv K, Wei S, Hu C (2019) Deplest: a blockchain-based privacy-preserving distributed database toward user behaviors in social networks. Inf Sci 100–117
Si H, Sun C, Li Y, Qiao H, Shi L (2019) Iot information sharing security mechanism based on blockchain technology. Future Gener Compute Syst 1028–1040
Kochovski P, Gec S, Stankovski V, Bajec M, Drobintsev PD (2019) Trust management in a blockchain based fog computing platform with trustless smart oracles. Future Gener Comput Syst 747–759
Ali M, Nelson J, Shea R, Freedman MJ (2016) Blockstack: a global naming and storage system secured by blockchains. In: 2016 USENIX annual technical conference (USENIX ATC ’16), pp 181–194
Narula N, Vasquez W, Virza M (2018) zkledger: privacy-preserving auditing for distributed ledgers. USENIX, pp 65–80
Fan K, Bao Z, Liu M, Vasilakos AV, Shi W (2020) Dredas: decentralized, reliable and efficient remote outsourced data auditing scheme with blockchain smart contract for industrial iot. Future Gener Comput Syst Int J Esci 665–674
Li L, Liua J, Changa X, Liu T, Liu J (2020) Toward conditionally anonymous bitcoin transactions: a lightweight-script approach. Inf Sci 290–303
Zhou Z, Wang B, Dong M, Ota K (2019) Secure and efficient vehicle-to-grid energy trading in cyber physical systems: integration of blockchain and edge computing. IEEE Trans Syst Man Cybern Syst 1–15
He S, Tang Q, Wu CQ, Shen X (2020) Decentralizing iot management systems using blockchain for censorship resistance. IEEE Trans Ind Inform 715–727
Kalapaaking AP, Khalil I, Atiquzzaman M (2022) Blockchain-enabled and multisignature-powered verifiable model for securing federated learning systems. IEEE Trans Internets Things. https://doi.org/10.1109/JIOT.2023.3289832
Matetic S, Wust K, Schneider M, Kostiainen K, Karame G, Capkun S (2019) Bite: bitcoin lightweight client privacy using trusted execution. In: 28th USENIX Security Symposium, pp 783–800
Oleksenko O, Trach B, Krahn R, Martin A, Fetzer C, Silberstein M (2018) Varys: protecting sgx enclaves from practical side-channel attacks. In: 2018 USENIX annual technical conference (USENIX ATC ’18), pp 227–239
Dave A, Leung C, Popa RA, Gonzalez JE, Stoica I (2020) Oblivious coopetitive analytics using hardware enclaves. In: EuroSys ’20: proceedings of the fifteenth European conference on computer systems
Zhao W, Lu K, Qi Y, Qi S (2020) Mptee: bringing flexible and efficient memory protection to intel sgx. In: EuroSys ’20: proceedings of the fifteenth European conference on computer systems, pp 1–15
Anati I, Gueron S, Johnson S (2013) Innovative technology for cpu based attestation and sealing. In: In Proceedings of the 2nd international workshop on hardware and architectural support for security and privacy
Corporation I (2014) Intel®software guard extensions programming reference. In: 329298-002us Edition
Zcash. https://z.cash (2017)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no competing interests to declare that are relevant to the content of this article.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Xie, H., Zheng, J., Zhang, Z. et al. TEDA: a trusted execution environment-and-blockchain-based data protection architecture for Internet of Things. Computing 106, 939–960 (2024). https://doi.org/10.1007/s00607-023-01253-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00607-023-01253-y