Abstract
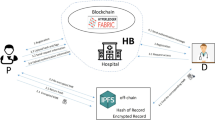
The blockchain-based Electronic Medical Record (EMR) data storage system encounters challenges which are data leakage, insufficient access control, and low retrieval efficiency. In response to these issues, this paper proposes a lightweight searchable encryption and access control system for sharing EMR data securely. The lightweight searchable encryption scheme which is achieved by integrating the trapdoor verification phase with the keyword retrieval phase is constructed using BGG13 + and MP12. User access control is implemented through a Boolean circuit to replace arithmetic operations and thus improve arithmetic efficiency. Since logic operations can reduce the computation time, this paper uses Boolean circuits for user rights verification implementation. In addition, this paper adopts the Bloom filter as the system index to enhance the efficiency of block-chain data retrieval. According to the simulation results, there is a performance advantage of this system over similar systems.









Similar content being viewed by others
Data availability
Enquiries about data availability should be directed to the authors.
References
Xu, S., Ning, J., Li, Y., Zhang, Y., Xu, G., Huang, X., Deng, R.H.: A secure EMR sharing system with tamper resistance and expressive access control. IEEE Trans. Dependable Secure Comput. 20, 53–67 (2023). https://doi.org/10.1109/TDSC.2021.3126532
Akinyele, J.A., Pagano, M.W., Green, M.D., Lehmann, C.U., Peterson, Z.N.J., Rubin, A.D.: Securing electronic medical records using attribute-based encryption on mobile devices. In: Proceedings of the 1st ACM workshop on Security and privacy in smartphones and mobile devices. pp. 75–86. Association for Computing Machinery, New York (2011)
Frakes, M., Jena, A.B.: Does medical malpractice law improve health care quality? J. Public Econ. 143, 142–158 (2016). https://doi.org/10.1016/j.jpubeco.2016.09.002
Ren, Y., Leng, Y., Qi, J., Sharma, P.K., Wang, J., Almakhadmeh, Z., Tolba, A.: Multiple cloud storage mechanism based on blockchain in smart homes. Futur. Gener. Comput. Syst. 115, 304–313 (2021). https://doi.org/10.1016/j.future.2020.09.019
Ren, Y., Leng, Y., Cheng, Y., Wang, J., Ren, Y., Leng, Y., Cheng, Y., Wang, J.: Secure data storage based on blockchain and coding in edge computing. MBE. 16, 1874–1892 (2019). https://doi.org/10.3934/mbe.2019091
Bitcoin: A Peer-to-Peer Electronic Cash System, https://bitcoin.org/en/bitcoin-paper
Saini, A., Wijaya, D., Kaur, N., Xiang, Y., Gao, L.: LSP: lightweight smart-contract-based transaction prioritization scheme for smart healthcare. IEEE Internet Things J. 9, 14005–14017 (2022). https://doi.org/10.1109/JIOT.2022.3145406
Islam, S.H., Mishra, N., Biswas, S., Keswani, B., Zeadally, S.: An efficient and forward-secure lattice-based searchable encryption scheme for the Big-data era. Comput. Electr. Eng. 96, 107533 (2021). https://doi.org/10.1016/j.compeleceng.2021.107533
Zhang, X., Xi, P., Liu, W., Peng, S.: EMRShareChain: a privacy-preserving emr sharing system model based on the consortium blockchain. In: Bansal, M.S., Cai, Z., Mangul, S. (eds.) Bioinformatics Research and Applications, pp. 343–355. Springer Nature Switzerland, Cham (2022)
Zhu, H., Guo, Y., Zhang, L.: An improved convolution Merkle tree-based blockchain electronic medical record secure storage scheme. J. Inf. Sec. Appl. 61, 102952 (2021). https://doi.org/10.1016/j.jisa.2021.102952
Sun, W., Sun, J., Wang, X., Sun, J., Chai, Y., Wang, L.: An Improved H-algorand consensus mechanism with credibility assessment applying in EMR storage system. IEEE Access. 10, 55164–55175 (2022). https://doi.org/10.1109/ACCESS.2022.3176944
Li, C., Dong, M., Li, J., Xu, G., Chen, X.-B., Liu, W., Ota, K.: Efficient medical big data management with keyword-searchable encryption in healthchain. IEEE Syst. J. 16, 5521–5532 (2022). https://doi.org/10.1109/JSYST.2022.3173538
Michalas, A.: The lord of the shares: combining attribute-based encryption and searchable encryption for flexible data sharing. In: Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing. pp. 146–155. Association for Computing Machinery, New York (2019)
Zhang, L., Zou, Y., Yousuf, M.H., Wang, W., Jin, Z., Su, Y., Seokhoon, K.: BDSS: blockchain-based data sharing scheme with fine-grained access control and permission revocation in medical environment. KSII Trans. Internet Inf. Syst. 16, 1634–1652 (2022)
Ge, X., Yu, J., Hao, R., Lv, H.: Verifiable keyword search supporting sensitive information hiding for the cloud-based healthcare sharing system. IEEE Trans. Industr. Inf. 18, 5573–5583 (2022). https://doi.org/10.1109/TII.2021.3126611
Zaghloul, E., Li, T., Mutka, M.W., Ren, J.: dd-MABE: distributed multilevel attribute-based EMR management and applications. IEEE Trans. Serv. Comput. 15, 1592–1605 (2022). https://doi.org/10.1109/TSC.2020.3003321
Boneh, D., Gentry, C., Gorbunov, S., Halevi, S., Nikolaenko, V., Segev, G., Vaikuntanathan, V., Vinayagamurthy, D.: Fully key-homomorphic encryption, arithmetic circuit ABE and compact garbled circuits. In: Nguyen, P.Q., Oswald, E. (eds.) Advances in Cryptology – EUROCRYPT 2014, pp. 533–556. Springer, Berlin (2014)
Micciancio, D., Peikert, C.: Trapdoors for lattices: simpler, tighter, faster, smaller. In: Pointcheval, D., Johansson, T. (eds.) Advances in Cryptology – EUROCRYPT 2012, pp. 700–718. Springer, Berlin (2012)
Micciancio, D., Regev, O.: Lattice-based cryptography. In: Bernstein, D.J., Buchmann, J., Dahmen, E. (eds.) Post-Quantum Cryptography, pp. 147–191. Springer, Berlin (2009)
Regev, O.: the learning with errors problem (Invited Survey). In: 2010 IEEE 25th Annual Conference on Computational Complexity. pp. 191–204 (2010)
Funding
The authors have not disclosed any funding.
Author information
Authors and Affiliations
Contributions
Conceptualization, HTL, NSM, CD. Methodology, HTL, NSM. Software, HTL. Validation, HTL. Formal analysis, HTL. Investigation, HTL. Resources, HTL. Writing—original draft preparation, HTL, NSM, CD. Writing—review and editing, HTL, NSM. Visualization, HTL. Supervision, NSM, CD. Project administration, HTL. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors have not disclosed any competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Luo, H., Mei, N. & Du, C. EMR sharing system with lightweight searchable encryption and rights management. Cluster Comput (2024). https://doi.org/10.1007/s10586-024-04294-w
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10586-024-04294-w