Abstract
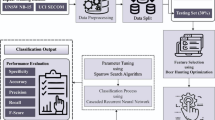
Anomaly detection (AD) in the industrial internet of things (IIoT) platform is said to be the major module of security the consistency, safety, and efficacy of industrial procedures. In IIoT, several sensors and devices always gather massive data counts from tools, infrastructure, and equipment. Ensuring the safety of IIoT AD systems is vital for protecting against cyber-attacks. AD and Intrusion detection are required to work in tandem to maintain industrial procedures. Machine learning (ML) and deep learning (DL) approaches generally employed for AD in IIoT. These methods allow automated AD and pattern detection. With this motivation, this study develops an enhanced pelican optimization model with an ensemble voting-based anomaly detection (EPOA-EVAD) approach. Primarily, the SMOTE approach is used for class imbalance data handling. The presented EPOA-EVAD technique integrates the EPOA-based feature selection and ensemble voting classifier to enhance the accuracy and efficiency of AD in IIoT environments. In addition, the group teaching optimization algorithm with SMOTE approach is used for the purpose of class imbalance data handling. EPOA optimally chooses the related features from the complex and high-dimensional IIoT data. For AD, the EPOA-EVAD technique involves an ensemble learning process comprising gated recurrent unit (GRU), bi-directional long short-term memory (BiLSTM), and stacked autoencoder (SAE). Lastly, the seagull optimization (SGO) algorithm fine-tunes the parameters compared with the DL approaches. The simulation values exhibited that the proposed system outperforms standard approaches, offering robust and adaptive AD capabilities in dynamic IIoT settings. The proposed EPOA-EVAD technique contributes to the advancement of AD techniques crucial for maintaining the integrity and efficiency of industrial processes in the era of IIoT.
















Similar content being viewed by others
Availability of data and material
(Data transparency).
Code availability
Code availability (software application or custom code).
References
Asgharzadeh, H., Ghaffari, A., Masdari, M., Gharehchopogh, F.S.: Anomaly-based intrusion detection system in the Internet of Things using a convolutional neural network and multi-objective enhanced Capuchin Search Algorithm. J. Parallel Distrib. Comput. 175, 1–21 (2023)
Wang, Y., Wang, J., Jin, H.: Network intrusion detection method based on improved CNN in internet of things environment. Mob. Inf. Syst. (2022). https://doi.org/10.1155/2022/3850582
Alshahrani, H., Khan, A., Rizwan, M., Reshan, M.S.A., Sulaiman, A., Shaikh, A.: Intrusion detection framework for industrial internet of things using software defined network. Sustainability 15(11), 9001 (2023)
Selim, G.E.I., Hemdan, E.E.D., Shehata, A.M., El-Fishawy, N.A.: Anomaly events classification and detection system in critical industrial internet of things infrastructure using machine learning algorithms. Multimedia Tools Appl. 80, 12619–12640 (2021)
Le, T.T.H., Oktian, Y.E., Kim, H.: XGBoost for imbalanced multiclass classification-based industrial internet of things intrusion detection systems. Sustainability 14(14), 8707 (2022)
Moustafa, N., Koroniotis, N., Keshk, M., Zomaya, A.Y., Tari, Z.: Explainable intrusion detection for cyber defences in the internet of things: opportunities and solutions. IEEE Commun. Surv. Tutor. 25(3), 1775–1807 (2023)
Zhang, Y., Yang, C., Huang, K., Li, Y.: Intrusion detection of industrial internet-of-things based on reconstructed graph neural networks. IEEE Trans. Netw. Sci. Eng. (2022). https://doi.org/10.1109/TNSE.2022.3184975
Alalayah, K.M., Alrayes, F.S., Alzahrani, J.S., Alaidarous, K.M., Alwayle, I.M., Mohsen, H., Ahmed, I.A., Al Duhayyim, M.: Optimal deep learning based intruder identification in industrial internet of things environment. Comput. Syst. Sci. Eng. 46(3), 3121 (2023)
Tharewal, S., Ashfaque, M.W., Banu, S.S., Uma, P., Hassen, S.M., Shabaz, M.: Research article intrusion detection system for industrial internet of things based on deep reinforcement learning. Wirel. Commun. Mob. Comput. (2023). https://doi.org/10.1155/2022/9023719
Rashid, M.M., Khan, S.U., Eusufzai, F., Redwan, M.A., Sabuj, S.R., Elsharief, M.: A federated learning-based approach for improving intrusion detection in industrial internet of things networks. Network 3(1), 158–179 (2023)
Li, S., Chai, G., Wang, Y., Zhou, G., Li, Z., Yu, D., Gao, R.: CRSF: an intrusion detection framework for industrial internet of things based on pretrained CNN2D-RNN and SVM. IEEE Access 11, 92041–92054 (2023)
Wang, X., Garg, S., Lin, H., Hu, J., Kaddoum, G., Piran, M.J., Hossain, M.S.: Toward accurate anomaly detection in industrial internet of things using hierarchical federated learning. IEEE Internet Things J. 9(10), 7110–7119 (2021)
Tharewal, S., Ashfaque, M.W., Banu, S.S., Uma, P., Hassen, S.M., Shabaz, M.: Intrusion detection system for industrial Internet of Things based on deep reinforcement learning. Wirel. Commun. Mob. Comput. 2022, 1–8 (2022)
Gopi, R., Sheeba, R., Anguraj, K., Chelladurai, T., Alshahrani, H.M., Nemri, N., Lamoudan, T.: Intelligent intrusion detection system for industrial internet of things environment. Comput. Syst. Sci. Eng. (2023). https://doi.org/10.32604/csse.2023.025216
Abdel-Basset, M., Chang, V., Hawash, H., Chakrabortty, R.K., Ryan, M.: Deep-IFS: intrusion detection approach for industrial internet of things traffic in fog environment. IEEE Trans. Ind. Inf. 17(11), 7704–7715 (2020)
Li, A., Yi, S.: Intelligent intrusion detection method of industrial Internet of things based on CNN-BiLSTM. In: Security and Communication Networks (2022).
Alhomoud, A.: An optimized network intrusion detection system for attack detection based on supervised machine learning models in an internet-of-things environment. Int. J. Adv. Soft Comput. Appl. (2023). https://doi.org/10.15849/IJASCA.230720.02
Long, J., Liang, W., Li, K.C., Wei, Y., Marino, M.D.: A regularized cross-layer ladder network for intrusion detection in industrial internet of things. IEEE Trans. Ind. Inf. 19(2), 1747–1755 (2022)
Ndichu, S., Ban, T., Takahashi, T., Inoue, D.: AI-assisted security alert data analysis with imbalanced learning methods. Appl. Sci. 13(3), 1977 (2023)
Abdelhamid, M., Kamel, S., Zeinoddini-Meymand, H.: Enhancing distribution generator impact mitigation using an adaptive protection scheme based on modified pelican optimization algorithm and active database management system. Energy Sci. Eng. 11(11), 4108–27 (2023)
Huang, J., Yang, S., Li, J., Oh, J., Kang, H.: Prediction model of sparse autoencoder-based bidirectional LSTM for wastewater flow rate. J. Supercomput. 79(4), 4412–4435 (2023)
Shiri, F.M., Perumal, T., Mustapha, N., Mohamed, R.: A Comprehensive Overview and Comparative Analysis on Deep Learning Models: CNN, RNN, LSTM, GRU. (2023). arXiv preprint arXiv:2305.17473.
Yu, Y., Li, J., Li, J., Xia, Y., Ding, Z., Samali, B.: Automated damage diagnosis of concrete jack arch beam using optimized deep stacked autoencoders and multi-sensor fusion. Dev. Built Environ. 14, 100128 (2023)
Jia, H., Xing, Z., Song, W.: A new hybrid seagull optimization algorithm for feature selection. IEEE Access 7, 49614–49631 (2019)
Kasongo, S.M., Sun, Y.: Performance analysis of intrusion detection systems using a feature selection method on the UNSW-NB15 dataset. J. Big Data 7(1), 1–20 (2020)
Kotecha, K., Verma, R., Rao, P.V., Prasad, P., Mishra, V.K., Badal, T., Jain, D., Garg, D., Sharma, S.: Enhanced network intrusion detection system. Sensors 21, 7835 (2021). https://doi.org/10.3390/s21237835
Zhou, X., Hu, Y., Liang, W., Ma, J., Jin, Q.: Variational LSTM enhanced anomaly detection for industrial big data. IEEE Trans. Ind. Inf. 17(5), 3469–3477 (2020)
Moldovan, D., Anghel, I., Cioara, T., Salomie, I.: Particle swarm optimization based deep learning ensemble for manufacturing processes. In: 2020 IEEE 16th International Conference on Intelligent Computer Communication and Processing (ICCP), pp. 563–570. IEEE
Chander, N., Upendra Kumar, M.: Metaheuristic feature selection with deep learning enabled cascaded recurrent neural network for anomaly detection in Industrial Internet of Things environment. Clust. Comput. 26(3), 1801–19 (2023)
Chander, N., Upendra Kumar, M.: Metaheuristics with deep convolutional neural network for class imbalance handling with anomaly detection in industrial IoT environment. J. Theor. Appl. Inf. Technol. 101, 10 (2023)
Adeyemo, V.E., et al.: Ensemble and deep-learning methods for two-class and multi-attack anomaly intrusion detection: an empirical study. Int. J. Adv. Comput. Sci. Appl. (2019). https://doi.org/10.14569/IJACSA.2019.0100969
Funding
No funding.
Author information
Authors and Affiliations
Contributions
The authors confirm contribution to the paper as follows: NC—study conception and design, data collection, analysis and interpretation of results, and manuscript preparation. Dr. MUK reviewed the results and approved the final version of the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chander, N., Upendra Kumar, M. Enhanced pelican optimization algorithm with ensemble-based anomaly detection in industrial internet of things environment. Cluster Comput (2024). https://doi.org/10.1007/s10586-024-04303-y
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10586-024-04303-y