Abstract
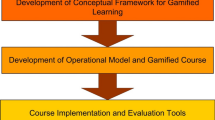
This research project aims to increase the employees' cybersecurity awareness by proposing a training program that consists of pre-game and post-game phishing attacks, pre-game and post-game surveys, and an interactive zero-day game with embedded threat scenarios. Furthermore, we propose five flowcharts that simulate common cyberattacks. The zero-day game consists of five levels. The first level trains employees in using complex passwords. Two levels cover the social engineering attacks: one level trains employees about suspicious links and online survey tricks, while the other level trains players about the organization's security policies. The fourth level educates employees about malware spread via repackaged fake applications. The last level educates employees about phishing email attacks. Furthermore, we developed a chatbot inside the game to aid users in playing the different game levels. Additionally, two surveys and two phishing attacks are carried out to assess the employees' knowledge level of cybersecurity threats. The zero-day cybersecurity awareness program is applied to twenty-three employees. Experimental results indicate that the zero-day cybersecurity awareness program is more engaging and effective than traditional awareness programs. Results also indicate that the proposed program accurately measures and improves the employees' cybersecurity awareness level.











Similar content being viewed by others
References
Zubair S et al (2023) A hybrid algorithm-based optimization protocol to ensure data security in the cloud. Int J Inf Technol. https://doi.org/10.1007/s41870-023-01546-7
Usoh M et al (2023) A hybrid machine learning model for detecting cybersecurity threats in IoT applications. Int J Inf Technol 15:3359–3370
Malhi M et al (2020) E-Learning based on cloud computing for educational institution. Int J Inf Technol 12(4):162–169
Alahmari S et al (2023) Moving beyond cyber security awareness and training to engendering security knowledge sharing. Inf Syst E Bus Manag 21(10):123–158
Hu S et al (2022) Security education, training, and awareness programs: literature review. J Comput Inform Syst 62(4):752–764
Opara EU et al (2021) Enterprise cyber security challenges to medium and large firms: an analysis. Int J Electron Inf Eng 13(2):77–85
(2018) 2018 data breach investigations report, 11th edition. Verizon, pp. 1–65
Giboney JS et al (2023) Know your enemy: conversational agents for security, education, training, and awareness at scale. Comput Secur 129(C):103207
Dash B et al (2022) An effective cybersecurity awareness training model: first defense of an organizational security strategy. Int Res J Eng Technol 9(4):1–6
Darraj E et al (2019) Artificial intelligence cybersecurity framework: preparing for the here and now with AI. In: European conference on cyber warfare and security, pp 132–141
Fung YC et al (2022) A chatbot for promoting cybersecurity awareness. Cyber Secur 370:379–387
Gundu T (2023) Chatbots: a framework for improving information security behaviours using ChatGPT. IFIP Adv Inf Commun Technol 674:418–431
Chandana HM et al (2018) Cognitive way of detecting cyberbullying in chatbots. Int J Adv Res Comput Sci 9(3):14–17
Syamsuddin I et al (2023) A novel AIML based chatbot for information security training. Artif Int Appl Netw Sys 724:297–305
Filippos G et al (2015) CyberAware: a mobile game-based app for cybersecurity education and awareness. In: International conference interactive mobile communication technologies and learning, pp 54–58
Alotaibi F et al (2017) Enhancing cybersecurity awareness with mobile games. In: 12th international conference internet technology secured transactions, pp 129–134
Ling L et al (2019) Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity behavior. Int J Inf Man 45:13–24
Hart S et al (2020) Riskio: a serious game for cyber security awareness and education. Comput Secur 95:1–18
Yasin A et al (2018) Design and preliminary evaluation of a cyber security requirements education game (SREG). Inf Softw Technol 95:179–200
Jin G et al (2018) Game based cybersecurity training for high school students. In: Proceedings of the 49th ACM technical symposium on computer science education, USA, pp 68–73
Abu-Amara F et al (2021) A novel SETA-based gamification framework to raise cybersecurity awareness. Int J Inf Technol. https://doi.org/10.1007/s41870-021-00760-5
Sophos (2020) https://www.sophos.com/en-us.aspx
Abu-Amara A et al (2021) Cyber shield security awareness program. In: 8th international conference on computing for sustainable global development, pp 422–425
Azhagiri M et al (2023) An intrusion detection system using ranked feature bagging. Int J Inf Technol. https://doi.org/10.1007/s41870-023-01621-z
Acknowledgements
The authors would like anonymous reviewers for their valuable feedback.
Funding
No funding was received to assist with the preparation of this manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest regarding the publication of this paper.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Abu-Amara, F., Hosani, R.A., Tamimi, H.A. et al. Spreading cybersecurity awareness via gamification: zero-day game. Int. j. inf. tecnol. (2024). https://doi.org/10.1007/s41870-024-01810-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s41870-024-01810-4